Securing your Hosted Payment Form
Familiarize yourself with best practices to help mitigate fraud on hosted payment forms.
Fraudsters are always looking for vulnerabilities that they can exploit to steal consumer payment data. As eCommerce evolves, so do payment preferences and digital spending habits. As a result, merchants need to exercise extra caution to protect themselves and their customers from being impacted by fraudulent activity. If a merchant is impacted by a fraudulent transaction, the merchant could bear financial responsibility for those transactions and may also suffer reputational damage.
When using our PayConex Hosted Payment Forms, we recommend multiple best practices to help mitigate attempted fraud. These steps help make your checkout process more secure and could prevent damages that might result from fraudulent transactions.
- Enable Google ReCaptcha
- Require CVV/AVS Verification
- Implement Transaction Velocity Checks
- Verify Users Prior to Displaying Payment Forms
- Temporarily Disable Vulnerable Forms
We encourage the usage of more than one mitigation method if possible. We recommend assessing your business model and then determining how best to combine multiple approaches to mitigate fraud. If you feel fraudsters are targeting your business, give us a call today at 800-675-6573 to speak with one of our experts.
Note
One additional item that you may want to consider is how your hosted payment form is rendered. If you are loading a hosted payment form from your server you will also want to review our article Using Hash with Hosted Payment Forms. This article outlines how to use hashed authentication to allow a server to render a hosted payment form.
Enable Google ReCaptcha
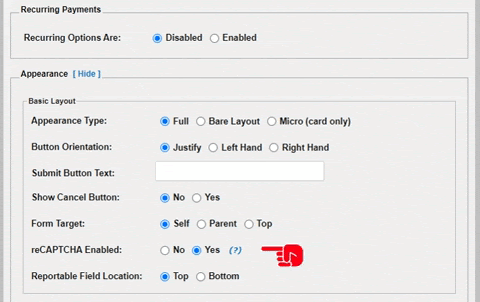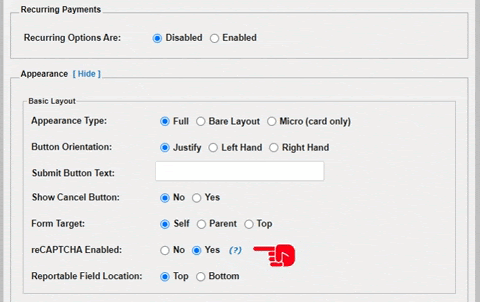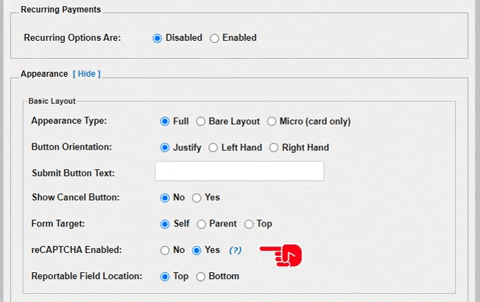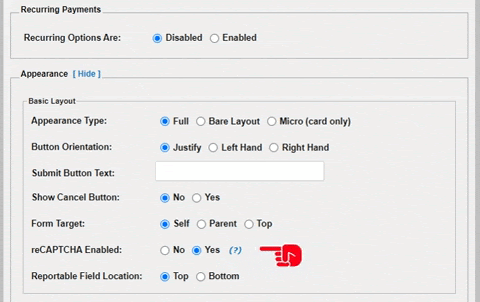
Google reCAPTCHAs are enabled on hosted payment forms by default. This feature enhances payment security by preventing automated bots or scripts from submitting payment forms. reCAPTCHA works by requiring users to click with a checkbox to prove they aren't a robot. If Google's reCAPTCHA service suspects the user is maliciously targeting the page then a simple puzzle is displayed, like asking the users to match words with images. To enable the feature or check its status, simply log into your PayConex account and navigate to your HPF configuration page.
Require CVV/AVS Verification
CVV stands for Card Verification Value or is commonly termed CVV2, CID or CVC. It adds another layer of protection to avoid credit card fraud. CVVs are harder to compromise than card numbers and expiration dates, so it's generally more secure to require them in your payment form.
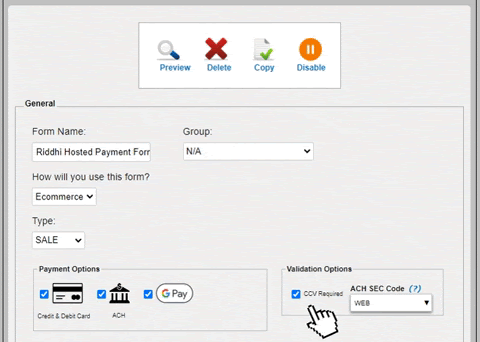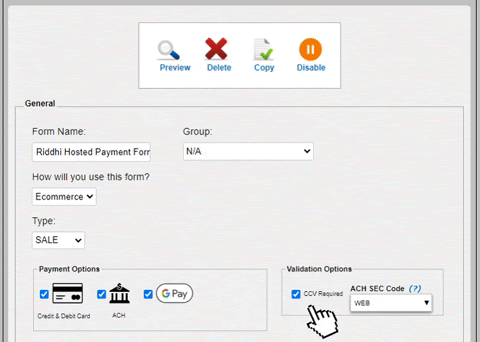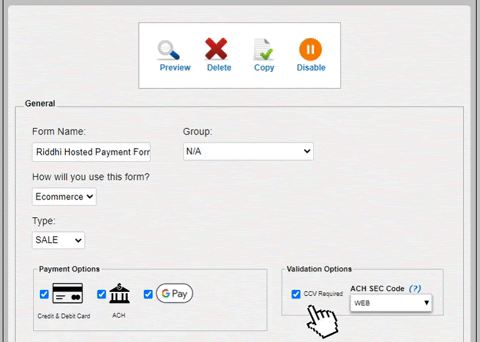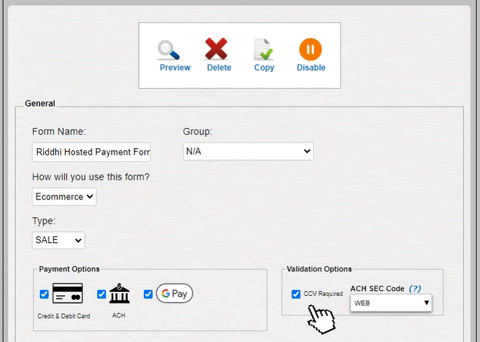
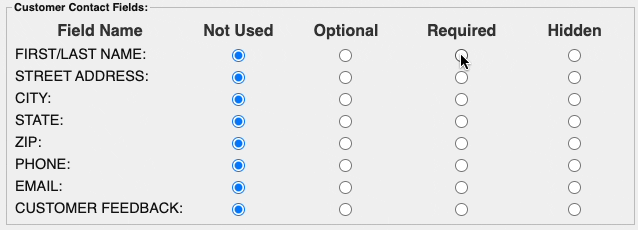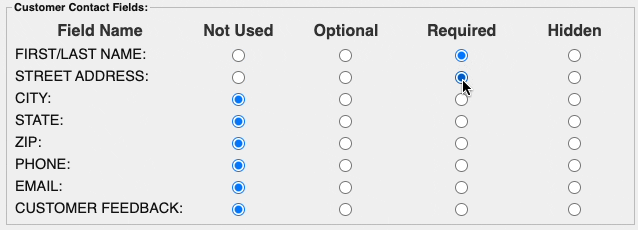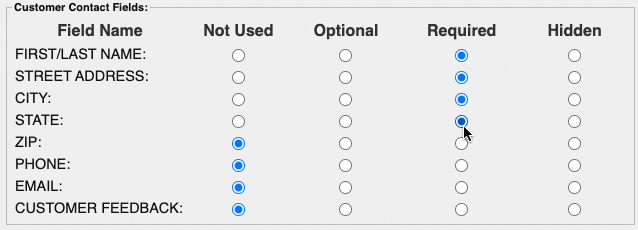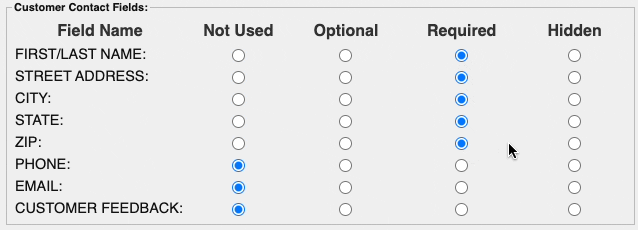
AVS stands for Address Verification Service, it is a validation code that card issuers will return to indicate if the address matches what the issuer has on file. In some cases, a card processor will actually decline transactions that do not return with the correct AVS response code. To make sure this AVS check is happening, it is recommended to require the input of the customer's name, address, city, state, and zip code. In the hosted payment form this can be enabled in the Customer Contact section of the settings.
Implement Transaction Velocity Checks
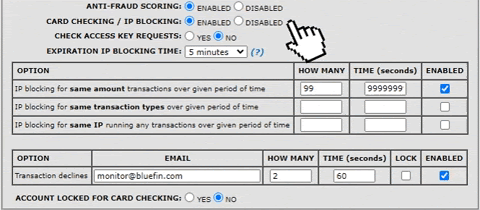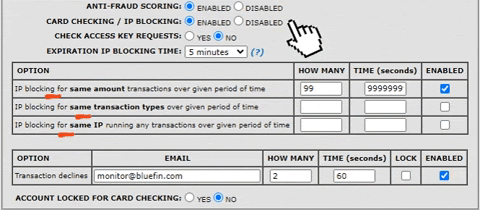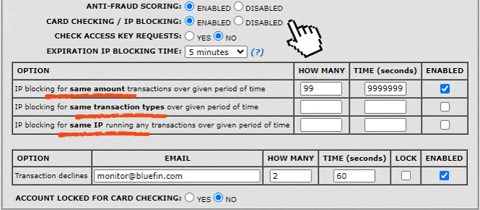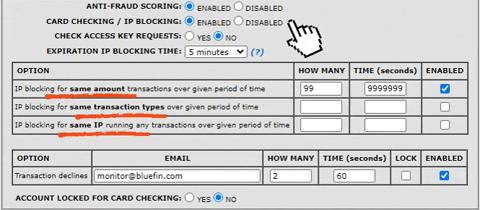
PayConex allows you to configure many options that will automatically block transactions coming from unwanted sources while allowing transactions coming from specific IPs that you are comfortable with. Two common indicators of fraud are groups of transactions with identical amounts and brief periods of unusually high traffic. These attacks often use the same attributes for the payment information. The PayConex blocking mechanisms allow you the ability to decline transactions that use the same amount, transaction type, or IP address that exceed a specific number within a specific time. We recommend merchants define their own rules to prevent these attacks. If you would like further assistance with these features please contact us at [email protected].
Verify Users Prior to Displaying Payment Forms
Another great way to prevent fraud on your Hosted Payment Form is to validate user sessions or require users to log in prior to accessing the form. If any user on a browser can access the payment form it can be susceptible to abuse by bad actors. This typically will manifest in the form of card testing fraud where a bad actor uses the payment page as a way to validate a list of stolen credit cards.
Temporarily Disable Vulnerable Forms
Attacks are always increasing in sophistication. Sometimes, even with all the security protocols, they can find a way to circumvent these safeguards. As a precaution, PayConex gives you the ability to disable a payment form if it's been compromised as a result of card testing attacks. This way, merchants can retain the page for future use without the need to delete the entire form.
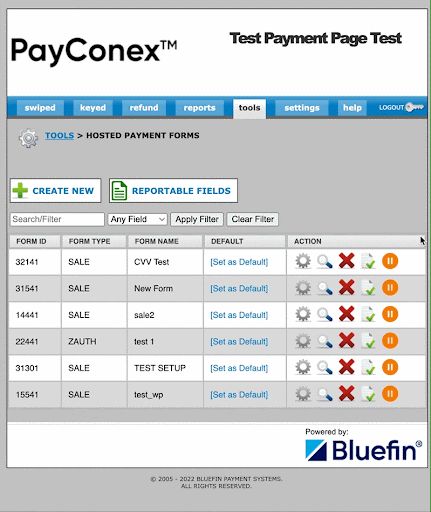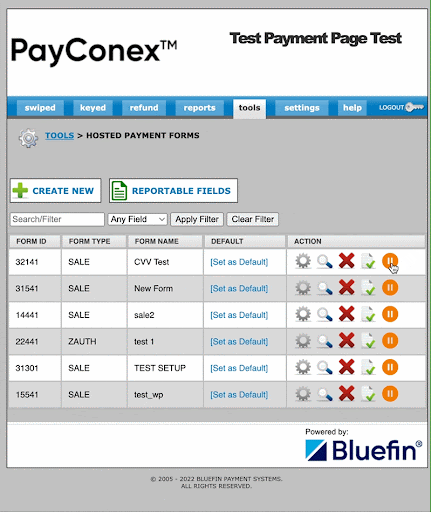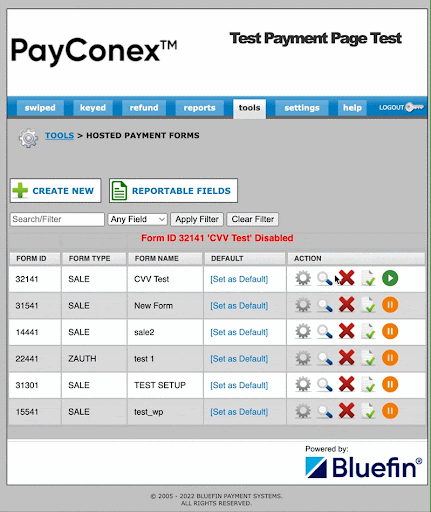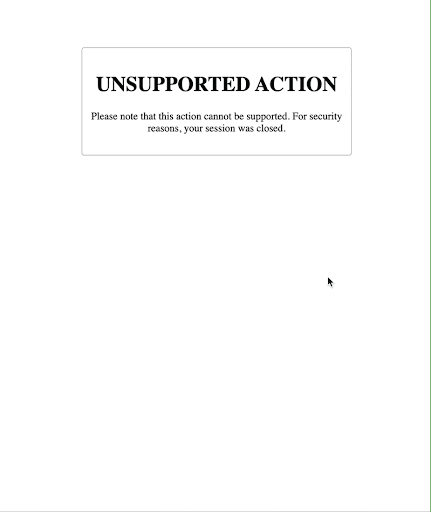
Bluefin recommends using one or more of the suggestions above to prevent unauthorized use of your PayConex hosted payment forms. Using Google reCaptcha, requiring CVV input, implementing velocity controls, verifying users, and temporarily disabling vulnerable forms are all viable ways a merchant can protect themselves from fraudulent attacks such as card testing.
We also offer additional paid services like 3D Secure and Fraud Scoring that aim to assist merchants with fraud prevention beyond what these best practices might cover.
Updated about 3 years ago
