Introduction
ShieldConex® Orchestration
Overview
Bluefin's ShieldConex® Orchestration enables you to take your data security to the next level.
ShieldConex® Orchestration is a vaultless secure data exchange API that provides and incorporates the powerful capabilities of ShieldConex® Tokenization (pass-through tokenization) and Decryptx® PCI-validated Point-to-Point Encryption (P2PE).
Through its secure unified API, it enables enterprise merchants to solve challenges like the following:
- Manage sensitive data internally while interacting with payment processors.
- Avoid processor lock-in.
- Manage multi-processor interactions.
ShieldConex® Orchestration leverages detokenization to seamlessly relay sensitive data embedded in JSON or XML messages between the merchant and the processor. It ensures secure and efficient data flow and next-level orchestration through its ability to extract P2PE payloads, perform decryption through Decryptx®, re-insert decrypted data into the message, and implement proxy authorization to the processor.
Visual Presentation
Before reading on, here is an illustrated video presentation of ShieldConex® Orchestration in a nutshell to get you started.
Visual Workflows
In addition to static images of workflow diagrams, all of the documentation of ShieldConex® Orchestration features interactive visual workflows with straight-forward creative animations breaking down each step of the respective ORCA use case with simplicity.
Check out the Use Cases below!
Orchestration
Terminology
In the ShieldConex® Orchestration solution, ORCA (derived from Orchestration) stands for Orchestration of Resilient Cybersecurity Architecture. This solution embodies a strong and dependable cybersecurity framework, designed to ensure robust protection for our clients.
In terms of naming API endpoints and JSON schema properties, we refer to ORCA as "proxy". This is because ShieldConex® Orchestration basically proxies the payment request data to the designated endpoint. For example, this is the base API endpoint for production environments: https://proxy.shieldconex.com. For all of the environments, check out API Endpoints.
Overview
Other orchestration offerings on the market provide a common API interface and then transform and translate the input data to the destination format. This approach requires these solutions to perform an integration and certification process to each of these destinations, which is resource-intensive and costly for the providers. It is also limiting as they need to code to the lowest common denominator; unique API fields and elements are generally not supported.
ShieldConex® Orchestration provides a more powerful solution. It relies on the client being integrated and certified with the endpoint provider. This could be an EMV integration with a payment processor or a card not present (CNP) level 3 (L-III) integration that transmits a lot of data to the payment processor. ShieldConex® Orchestration handles only the specific fields that require actioning, leaving all other data untouched.
In the case of an EMV transaction, Bluefin applies its P2PE service to encrypt the cardholder data in the payment terminal and decrypt it on the fly using ShieldConex® Orchestration in combination with Bluefin's Decryptx® solution. The decrypted data is then inserted into the message and sent securely over TLS to the payment processor for authorization. The response from the processor is proxied back to the client.
For CNP use (eCommerce or MO/TO), a ShieldConex® token is detokenized by ShieldConex®, and the cardholder data is reinserted into the message and sent to the processor for approval. The response from the processor is proxied back to the client.
The most powerful aspect of ShieldConex® Orchestration is that it can be used with any endpoint on the internet (see below). The solution can be used for payments, healthcare, and PII and PHI data.
Once ShieldConex® Orchestration is configured to support the client's application, it can be used immediately. ShieldConex® Orchestration functions like an extension of the client's environment.
Integration to Endpoints
As mentioned above, ShieldConex® Orchestration leverages the integration work already performed by the client.
For example, if the client has an appliance on their local network for decrypting or detokenizing data before sending it to the processor, this would be invisible to the processor; it would simply be a normal part of good security practice. The difference with ShieldConex® Orchestration is that the decryption or detokenization of data takes place in Bluefin's PCI DSS environment. The client no longer has sensitive data (PCI/PII/PHI) in their environment, which results in massive PCI scope reduction.
Decryptx®
Decryptx® is a sophisticated and secure data decryption solution designed to streamline the decryption process while ensuring maximum data security. This enables processors, payment gateways, and software platforms to universally connect to Bluefin and offer our PCI-validated P2PE solution directly to their clients.
Key Benefits of ShieldConex® Orchestration
- Reduce and remove PCI compliance overhead using tokenization across the entire payment process.
- Faster time-to-market and lower maintenance costs with our unified API.
- Full payment processor flexibility to mix and match processors as needed.
- Unified and universal tokens that work in all use cases.
- Increased scalability and reliability options for your system architecture.
Key Features of ShieldConex® Orchestration
-
Real-time tokenization and detokenization:
- The gateway automatically tokenizes and detokenizes discrete elements in the payload.
- ShieldConex® Orchestration offers on-the-fly tokenization and detokenization, providing a swift and secure process for data transmission to endpoints.
-
Real-time point-to-point encryption and decryption:
- ShieldConex® Orchestration excels in real-time decryption of PCI-validated cardholder data through a secure channel to the processor endpoint.
-
Format-preserving token generation:
- ShieldConex® Orchestration generates format-preserving tokens directly from EMV/P2PE transactions, ensuring compatibility and security.
-
Secure communication:
- Shares sensitive tokenized data seamlessly with partners and affiliates, enhancing collaboration while maintaining data security.
-
Bluefin keys in payment terminals:
- Gives merchants the flexibility to switch between processors without rekeying terminals, optimizing operational efficiency.
- This also allows merchants to switch between payment processors without refreshing all devices in the field.
-
Secure iframe integration:
- A secure iframe means that cardholder data can be easily collected from the merchant's website. Bluefin returns tokens, allowing them to be used for payments via any processor through ShieldConex® Orchestration.
-
Auto-tokenization of EMV-derived PAN:
- ShieldConex® Orchestration introduces a new innovation: auto-tokenization capabilities. It tokenizes the primary account number (PAN) extracted from EMV payloads. Merchants can then harness the generated tokens for secure and efficient handling of CNP transactions. This ShieldConex® BFID is included in the response headers. To enable this feature for your ORCA integration, please contact our Bluefin Technical Team.
-
Multi-processor support:
- ShieldConex® Orchestration works with all payment processors, thus delivering processor independence. Tokens work with any processor, so no more exporting and importing tokens when changing processors.
-
P2PE independence:
- Utilize any of Bluefin's more than 125 P2PE devices that are EMV-certified by the processor. Bluefin covers the P2PE and forwards SALE to the processor.
-
Data support:
- ShieldConex® Orchestration can be used with all payment processing, PII, and PHI data, and can handle any sensitive messaging data.
-
Multi-processor tokens:
- The same ShieldConex® Orchestration-generated token can be used on any processor, meaning that you own your own tokens, and don't need to convert tokens if you change processor.
-
Reduce e-tailer PCI scope:
- The iframe ShieldConex® Orchestration can be used to reduce PCI scope to a self-assessment questionnaire (SAQ)-A and to qualify for SAQ-P2PE processing payment without the need for a clear-text PAN in your environment.
-
Multiple supported processing forms:
- Ecommerce, CNP and EMV/P2PE processing are all supported.
-
Irreversible tokenization and time-boxed detokenization:
- Enhanced GDPR compliance support with new irreversible tokenization, timed token activation, and timed token deactivation. This provides better compliance with GDPR regulations by ensuring sensitive data is handled appropriately. See here for more on this feature: Irreversible Tokenization and Time-Boxed Detokenization.
-
ORCA Credential Vault
- ShieldConex Orchestration offers a Credential Vault option that lets you securely manage and rotate credentials used within ShieldConex Orchestrations—without requiring code changes or redeployments.
- For more information on its usage, refer to ORCA Credentials Vault.
-
Dynamic URL Path Support
- ShieldConex ORCA API supports a configurable HTTP header that allows clients to dynamically set the URL path used in downstream calls.
- For more information on this use case, refer to ORCA Credentials Vault.
-
Expanded Transformation Capabilities
- Orchestrations can apply transformation steps to downstream API responses before returning them to the caller. This enables response-side protection and normalization workflows that previously required custom middleware or downstream system changes.
- Protect sensitive data returned by third parties by tokenizing values returned by the payment processor.
- Keep tokenization at the orchestration boundary, so applications don't need to handle raw sensitive values.
- For the comprehensive section on this, refer to ShieldConex | ORCA Request and Response Actions.
- Orchestrations can apply transformation steps to downstream API responses before returning them to the caller. This enables response-side protection and normalization workflows that previously required custom middleware or downstream system changes.
These features collectively establish ShieldConex® Orchestration as a comprehensive solution, offering real-time security, flexibility, and collaboration capabilities in managing payment data between merchants and processors.
Conclusion
Thanks to the ShieldConex® Portal and the P2PE Manager, you enjoy complete visibility into transactions and how they are processed, as well as chain-of-custody, asset management, and device attestation capabilities. The ServiceNow app or P2PE management can also be used on top of ShieldConex® Orchestration.
See here for further information on the ShieldConex® tokenization service.
Explore the Decryptx® Parser here.
Use Cases
Iframe-based secure tokenization and detokenization processing
By using our embedded iframe approach to protect user interactions, you can avoid PCI and other compliance issues by working only with Bluefin tokens. Sensitive payment data, PII and PHI can be captured within the iframe, meaning that you avoid the need to handle this data in your systems. Instead, our iframe solution immediately tokenizes the sensitive data. All tokens are made available in one Bluefin API call, and can be used as-is for processor API interactions via the ShieldConex® Orchestration API.
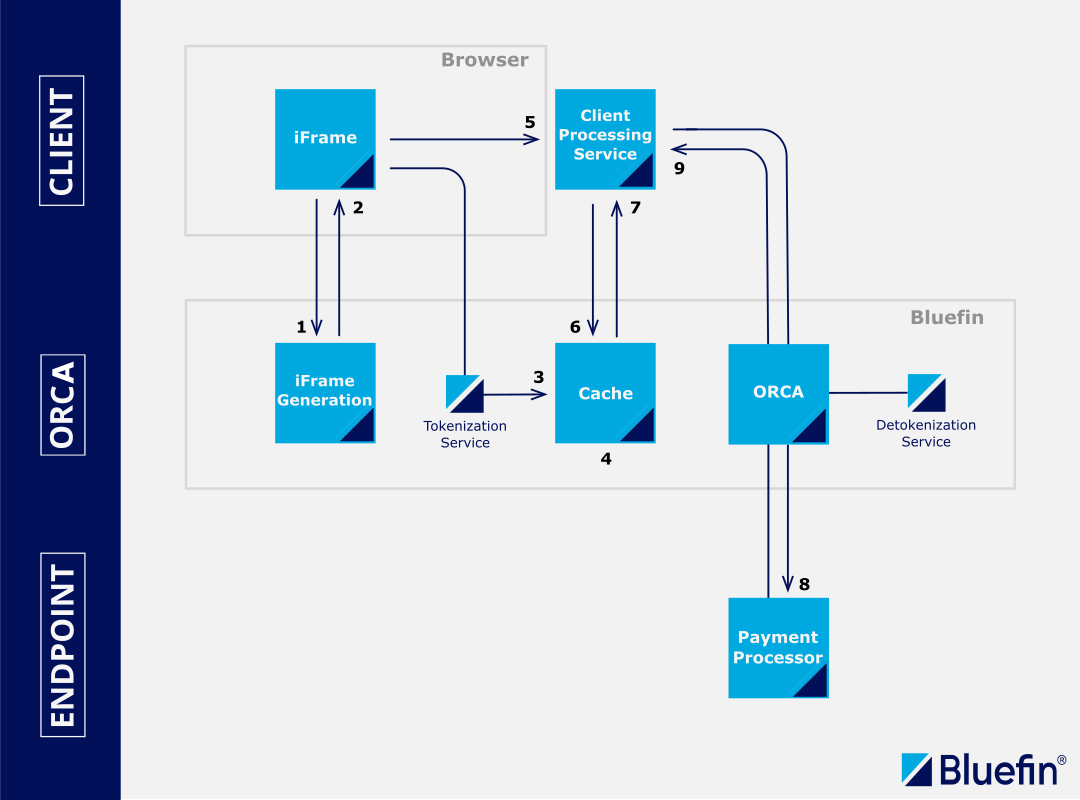
iframe-Based Secure Tokenization/Detokenization Processing
Sensitive data is collected safely using the ShieldConex® iframe. The client retrieves tokenized data, and using ShieldConex® Orchestration, the tokens - along with additional payload elements - are sent for detokenization. This secure processing mode ensures that the client never directly handles sensitive data.
Check out the Example Use Cases page for an in-depth look at the Iframe-Based Secure Tokenization/Detokenization Processing use case (sample source code included).
- (1 and 2) Consumer opens up client website and ShieldConex® iframe elements are loaded into the consumer’s browser.
- (3) After consumer enters data into the iframe elements, they are captured directly by ShieldConex® and tokenized. A BFID (Bluefin ID) is returned.
- (4) Tokens are cached in ShieldConex® for a maximum of one hour.
- (5) All data needed to complete the transaction, including the BFID, is sent to the client's processing service.
- (6 and 7) Using the BFID, the client requests their tokens and they are returned.
- (8) The client sends the message to ShieldConex® in the format required by their processor with the tokens in place rather than PANs (credit card). ShieldConex® Orchestration detokenizes the tokens, reinserts the actual PAN data into the payload, and relays the payment request to the processor.
- (9) The response is proxied back to the client.
- It is critical that merchant encrypts all the sensitive data of the payment processor response, preventing any sensitive data to ever enter the merchant envinroment. ShieldConex Orchestration offers this feature by specifying
responseActionsin an ORCA configuration. This is detailed out in the ShieldConex | ORCA Request and Response Actions section.
- It is critical that merchant encrypts all the sensitive data of the payment processor response, preventing any sensitive data to ever enter the merchant envinroment. ShieldConex Orchestration offers this feature by specifying
API-Based Tokenization and Detokenization Processing
The orchestrated approach allows you to fully replace all sensitive data in your system with our tokens. Because the Orchestration API provides transparent detokenization, no changes to existing business logic are needed, and the tokens can be used as in-place substitutes. Our API allows you to perform a staged migration to tokens without disrupting your system integrations.
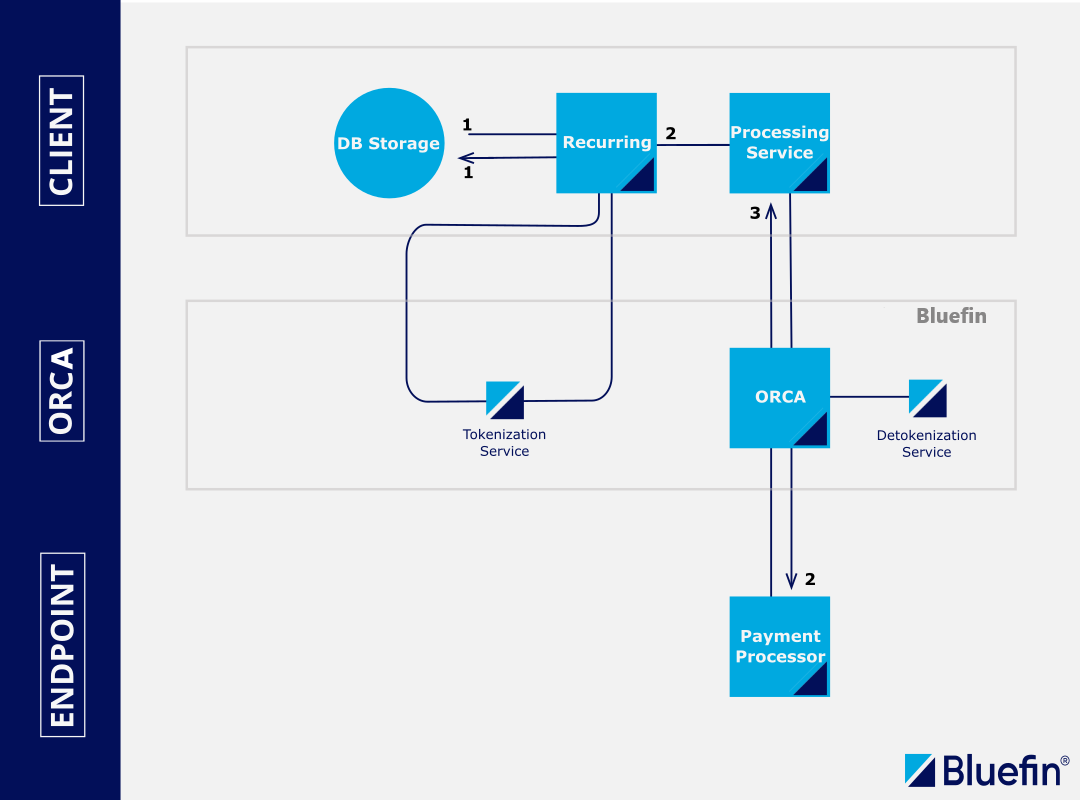
API-Based Tokenization and Detokenization Processing
This method outlines the straightforward integration of tokenization and detokenization into your API workflow using ShieldConex® services. By utilizing this service, your application gains enhanced security without the complexity of manually managing sensitive data. ShieldConex® implements robust Bluefin security measures, including PCI compliance and data protection, thus alleviating security concerns in your app.
- (1) Client tokenizes all cards on file by pulling them from their database, calling the ShieldConex® tokenization service APIs, and reinserting the tokens in their database. This "devalues" the sensitive data stored. The token and a BFID are returned for storage.
- (2) During the billing cycle, the client retrieves the ShieldConex® token and BFID from storage and sends them to ShieldConex® Orchestration in the format required by their processor with the tokens in place rather than PANs (credit card). ShieldConex® Orchestration detokenizes the tokens, reinserts the actual PAN data into the payload, and relays the payment request to the processor.
- (3) The response is proxied back to the client.
- It is critical that merchant encrypts all the sensitive data of the payment processor response, preventing any sensitive data to ever enter the merchant envinroment. ShieldConex Orchestration offers this feature by specifying
responseActionsin an ORCA configuration. This is detailed out in the ShieldConex | ORCA Request and Response Actions section.
- It is critical that merchant encrypts all the sensitive data of the payment processor response, preventing any sensitive data to ever enter the merchant envinroment. ShieldConex Orchestration offers this feature by specifying
This example is for recurring calls, but also works for any on-demand tokenization or detokenization processes.
PointConex Use Case
Overview
Bluefin offers the PointConex integration with a wide range of Bluefin-P2PE certified devices.
Terminology
In the POIntConex term, POI stands for Point of Interaction device that represents the hardware and software of the Point of Sale systems.
PointConex is a bundle solution supporting payment terminal decryption and orchestration to the payment processor (target destination).
This bundle consists of:
-
POI (Point of Interaction) device (terminal)
- Our Orchestration API also handles encrypted cardholder information (e.g. PAN) from third-party sources (such as payment terminals). As with the tokenization use cases, using our Decryptx® service, you can incorporate device payload parsing in an ORCA. Once again, you are freed from PCI compliance costs because you can send encrypted data via the Orchestration API, which we then decrypt for you in real time and send on the processor. At no stage does decrypted data enter your systems.
-
ShieldConex® Orchestration
- The P2PE encrypted payload is sent to the ShieldConex® ORCA via ORCA API.
- Forwarding the decrypted P2PE payload to the payment processor endpoint, securely over the TLS protocol.
- The response is proxied back to the client.
-
Decryptx® P2PE Solution
- P2PE Data encryption, extraction, and decryption: Decryptx® Parser + Decryptx®
- Decryptx® P2PE employs advanced encryption methods like SRED to secure cardholder data at the point of interaction/sale. By integrating ShieldConex® Orchestration, Decryptx® efficiently decrypts P2PE payloads in accordance with processor specifications, facilitating seamless authorization processing. This robust combination ensures PCI compliance and safeguards sensitive information throughout the payment processing journey.
The PointConex Integration incorporates all the features of ShieldConex® Orchestration and Decryptx® from the get-go, constituting the complete and flexible payment device solution for the merchant provided by Bluefin.
Among many others, the most notable feature for this integration is P2PE Independence:
- Utilize any of Bluefin's more than 125 P2PE devices that are EMV-certified by the processor. Bluefin covers the P2PE and forwards SALE to the processor.
For all the ShieldConex® ORCA key features, check out the Key Benefits of ShieldConex® Orchestration and Key Features of ShieldConex® Orchestration sections.
Portability
Whether the device is fully integrated, semi-integrated, or countertop, PointConex integration is predicated on the ShieldConex® Orchestration with Decryptx®.
Device Support
For the comprehensive list of Bluefin-P2PE certified devices, check out:
PointConex Integrations
The PointConex Use Case is divided into three scenarios based on how the POI device is integrated with the POS system. In all cases, EMV transactions are initiated at the terminal and encrypted using P2PE on hardware-level. These cases all involve EMV and P2PE Processing.
- Direct POI Device Integration
- Transactions are initiated and transmitted directly from the POI device without any intermediary POS system.
- Controller-Mediated Integration
- Transactions from either the POI device or POS system are routed through a corporate switch or controller, which manages communication and formatting before forwarding.
- POS-Connected POI Integration
- Transactions are initiated on a POS system that is physically or logically connected to the POI device. The POI device handles the encryption and transmission.
EMV Transaction Payload
As described in the Orchestration Introduction above, ShieldConex® Orchestration relies on the client being integrated and certified with the endpoint provider. This could be an EMV integration with a payment processor or a card not present (CNP) level 3 (L-III) integration that transmits a lot of data to the payment processor. ShieldConex® Orchestration handles only the specific fields that require actioning, leaving all other data untouched.
For example, ShieldConex® Orchestration ignores the transaction amount, currency, and transaction identifier that are specified to be left untouched for another transaction, but they still would be present in the payload. The merchant has the flexibility to specify API fields and elements according to their needs. Of course, we can choose to mask this data in our ORCA configuration for additional security purposes.
PointConex Example Use Case
The practical example use case, with ORCA configurations and device transaction payloads, that is applicable to all of these three integrations is the PointConex Example Use Case | EMV Transaction Orchestration.
As detailed above, it is just a matter of how the POI device is integrated with the POS system where the device-to-processor communication with ShieldConex® ORCA and Decryptx® workflow remains as versatile.
Direct POI Device Integration
- (1) The client inputs the EMV transaction details into the POI device (payment terminal). Bluefin applies the P2PE service to encrypt the cardholder data on hardware-level in the POI device using SRED.
- (2) ShieldConex® Orchestration extracts the P2PE payload through the Decryptx® Parser and decrypts it on the fly in combination with Bluefin's Decryptx® solution.
- (3) The decrypted data is then inserted into the message and sent securely over the TLS protocol to the payment processor for authorization.
- (4) The response from the processor is proxied back to the client, specifying whether the transaction has failed or succeeded, for example.
- It is critical that merchant encrypts all the sensitive data of the payment processor response, preventing any sensitive data to ever enter the merchant envinroment. ShieldConex Orchestration offers this feature by specifying
responseActionsin an ORCA configuration. This is detailed out in the ShieldConex | ORCA Request and Response Actions section.
- It is critical that merchant encrypts all the sensitive data of the payment processor response, preventing any sensitive data to ever enter the merchant envinroment. ShieldConex Orchestration offers this feature by specifying
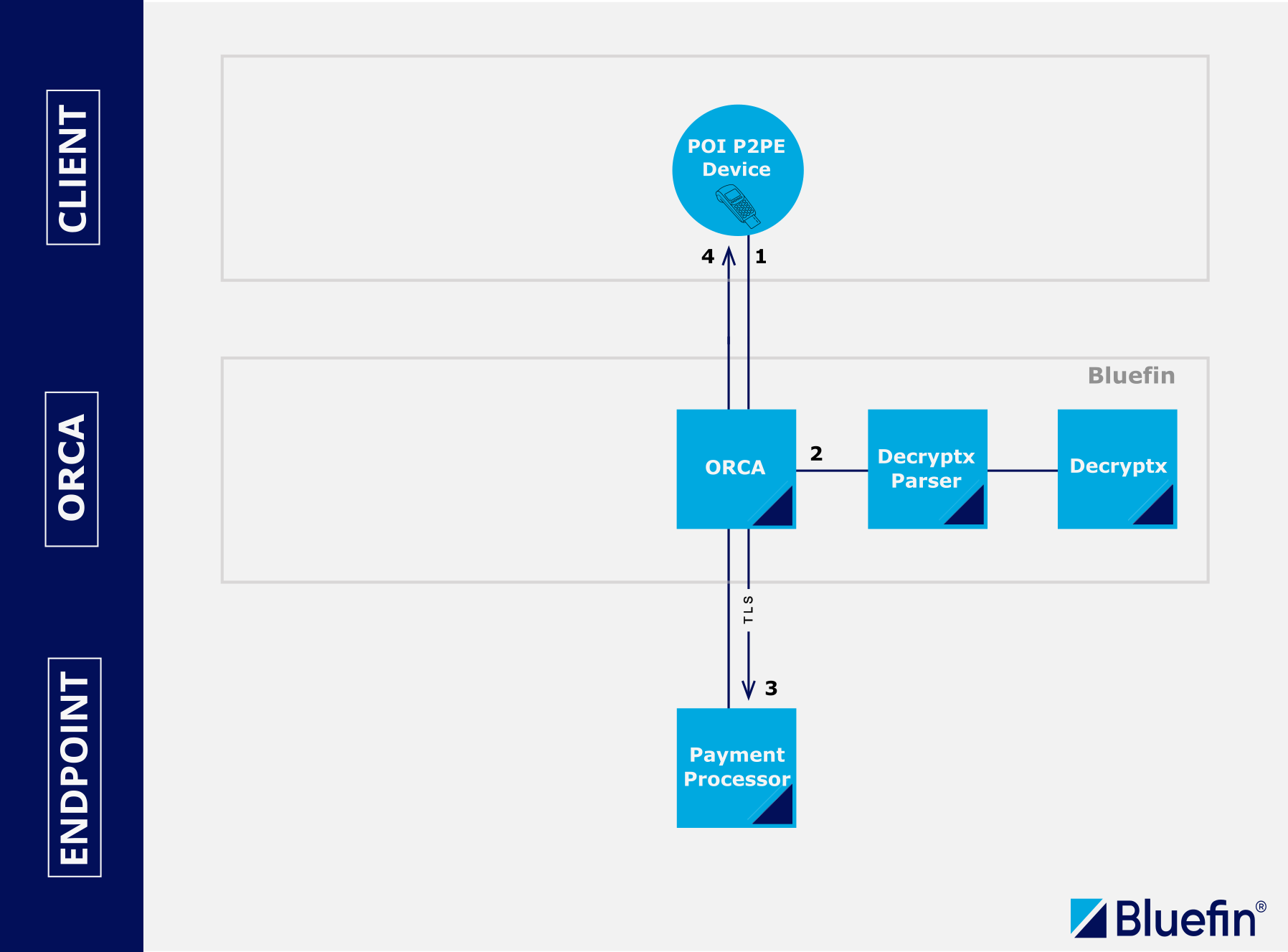
Direct POI Device Integration
Controller-Mediated Integration
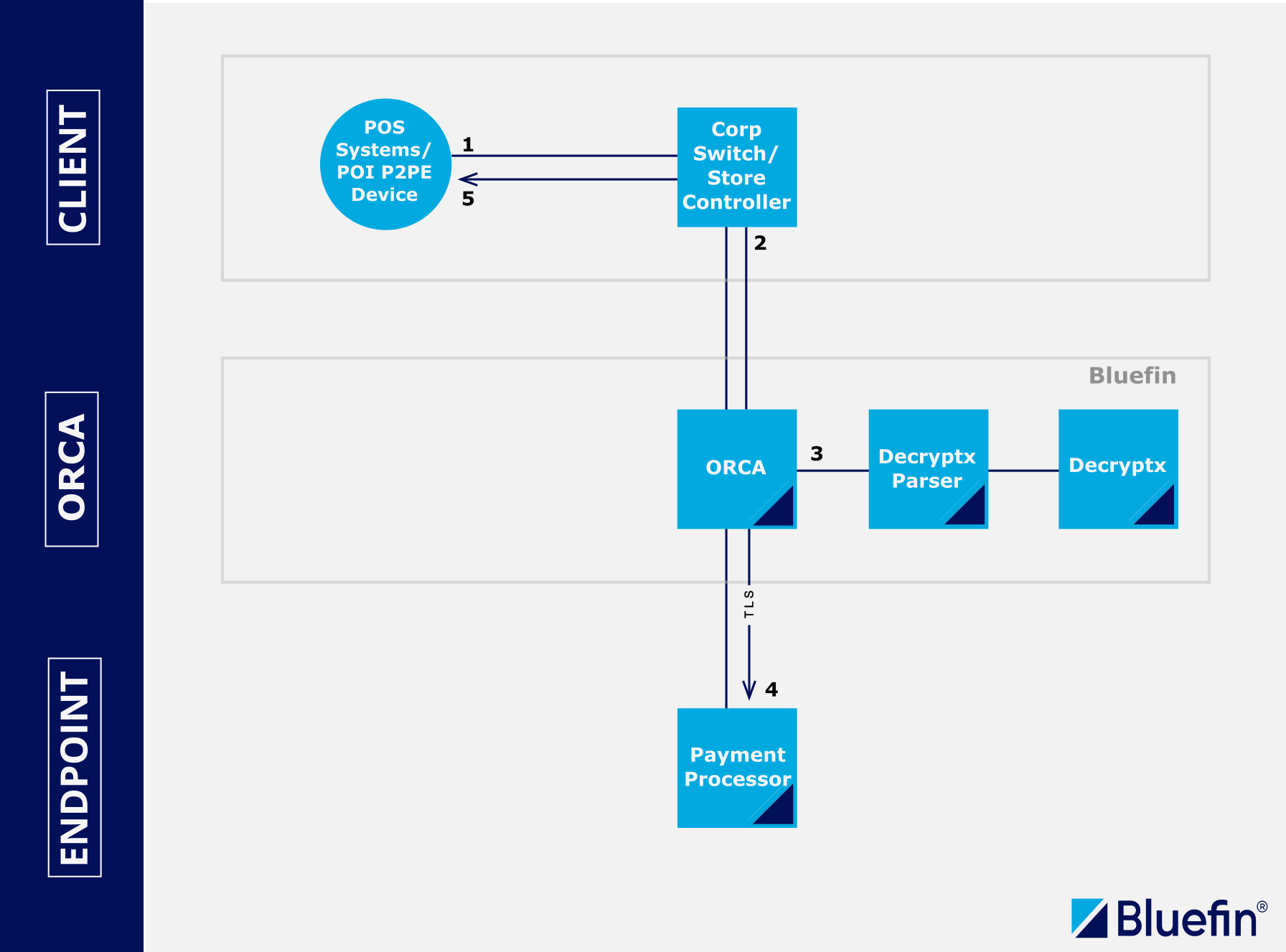
Controller-Mediated Integration
-
(1) PAN data is encrypted inside the point of interaction/sale device using SRED. The payload is forwarded to a corporate switch or controller for formatting.
-
(2) The P2PE payload is sent to ShieldConex® Orchestration, in the format required by the processor’s specification, for authorization.
-
(3) ShieldConex® finds the data elements in the message to properly decrypt the payload. The data is extracted and sent via the Decryptx® Parser to Decryptx®. The decrypted elements are returned to the Orchestration API and inserted into the message. (P2PE is complete at this point.)
-
(4) The message is forwarded securely over the TLS protocol to the payment processor for authorization.
-
(5) The response is proxied back to the client.
- It is critical that merchant encrypts all the sensitive data of the payment processor response, preventing any sensitive data to ever enter the merchant envinroment. ShieldConex Orchestration offers this feature by specifying
responseActionsin an ORCA configuration. This is detailed out in the ShieldConex | ORCA Request and Response Actions section.
- It is critical that merchant encrypts all the sensitive data of the payment processor response, preventing any sensitive data to ever enter the merchant envinroment. ShieldConex Orchestration offers this feature by specifying
POS-Connected POI Integration
As pointed out in the PointConex Use Case | Overview, Decryptx® ensures PCI compliance and safeguards sensitive information throughout the payment processing journey.
- (1) POI device connected to the POS systems, Bluefin-P2PE certified device, applies the P2PE service to encrypt the cardholder data on hardware-level in the payment terminal using SRED. This can also be referred to as POS systems hardware and software.
- (2) Via the ORCA API, the P2PE-encrypted payload is sent to the ShieldConex® ORCA.
- (3) ShieldConex® ORCA communicates and works with the Bluefin's Decryptx® Solution to preprocess and reinsert the P2PE payload. To see how these encrypted payloads are configured and sent in practice, refer to the JSON Decryptx® or XML Decryptx® API examples.
- (4) The decrypted payload is then inserted into the message and sent securely over the TLS protocol to the payment processor for authorization.
- (5) The response from the processor is proxied back to the client, specifying whether the transaction has failed or succeeded. On the way back, ShieldConex® Orchestration can also apply Auto-tokenization of EMV-derived PAN (see above). This can be used for recurring CNP payments.
- It is critical that merchant encrypts all the sensitive data of the payment processor response, preventing any sensitive data to ever enter the merchant envinroment. ShieldConex Orchestration offers this feature by specifying
responseActionsin an ORCA configuration. This is detailed out in the ShieldConex | ORCA Request and Response Actions section.
- It is critical that merchant encrypts all the sensitive data of the payment processor response, preventing any sensitive data to ever enter the merchant envinroment. ShieldConex Orchestration offers this feature by specifying
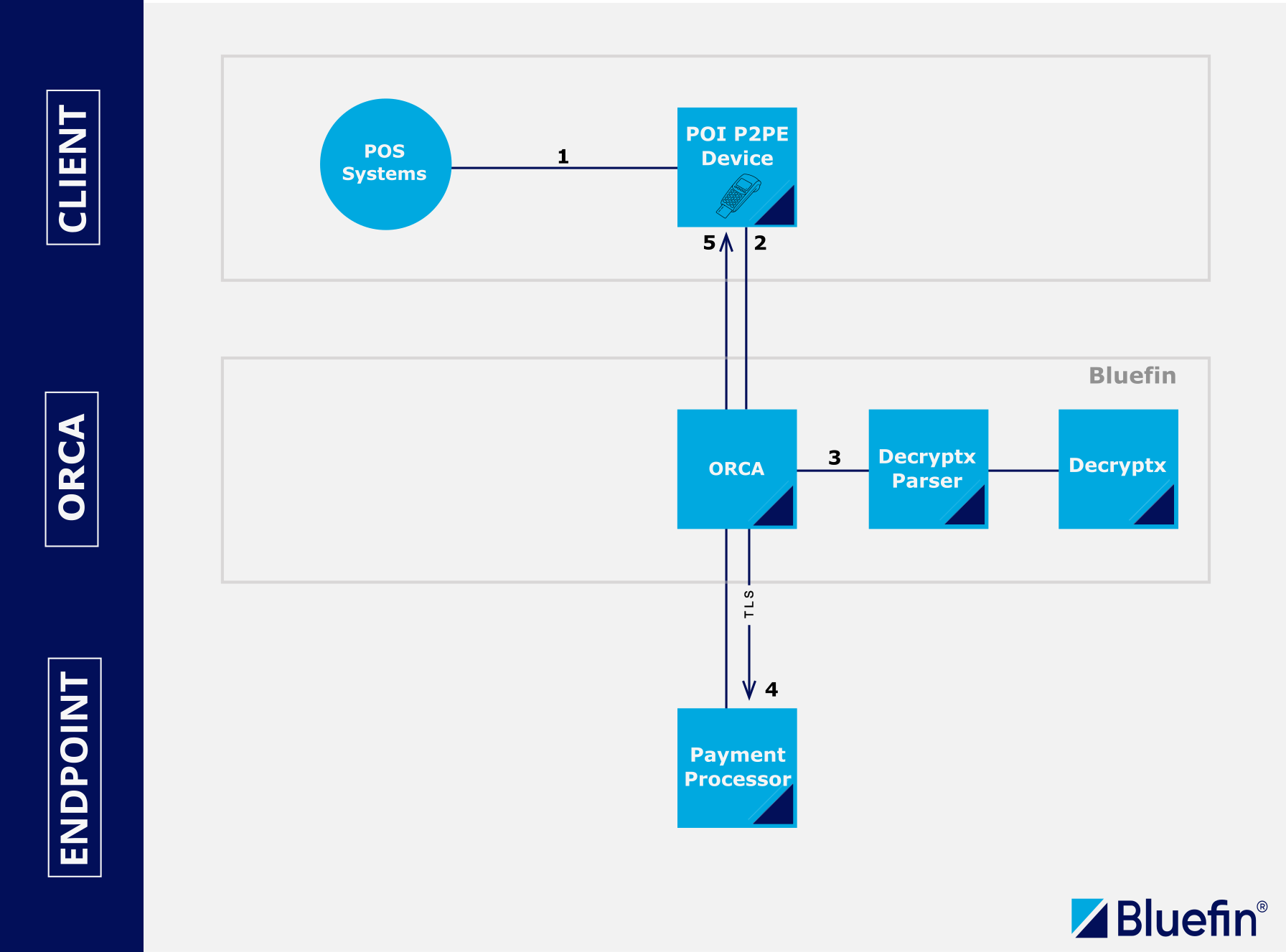
POS-Connected POI Integration
Fraud Services
All the benefits that apply to payment processors also apply to third party fraud services. Because you can now use the ShieldConex® Orchestration API to access fraud services, and use tokenization to insulate yourself from sensitive data, you get the same flexibility as with payment processors: reduced or eliminated PCI/PII/PHI compliance, no service lock-in, and more robust scalability and failover, along with many others.
Previously: transaction data is sent to the payment provider. The payment provider makes an API call to the fraud service. The fraud service approves or declines based on the fraud score.
With ShieldConex® Orchestration: an API call is made to a fraud provider via ShieldConex® Orchestration using ShieldConex® tokenized data.
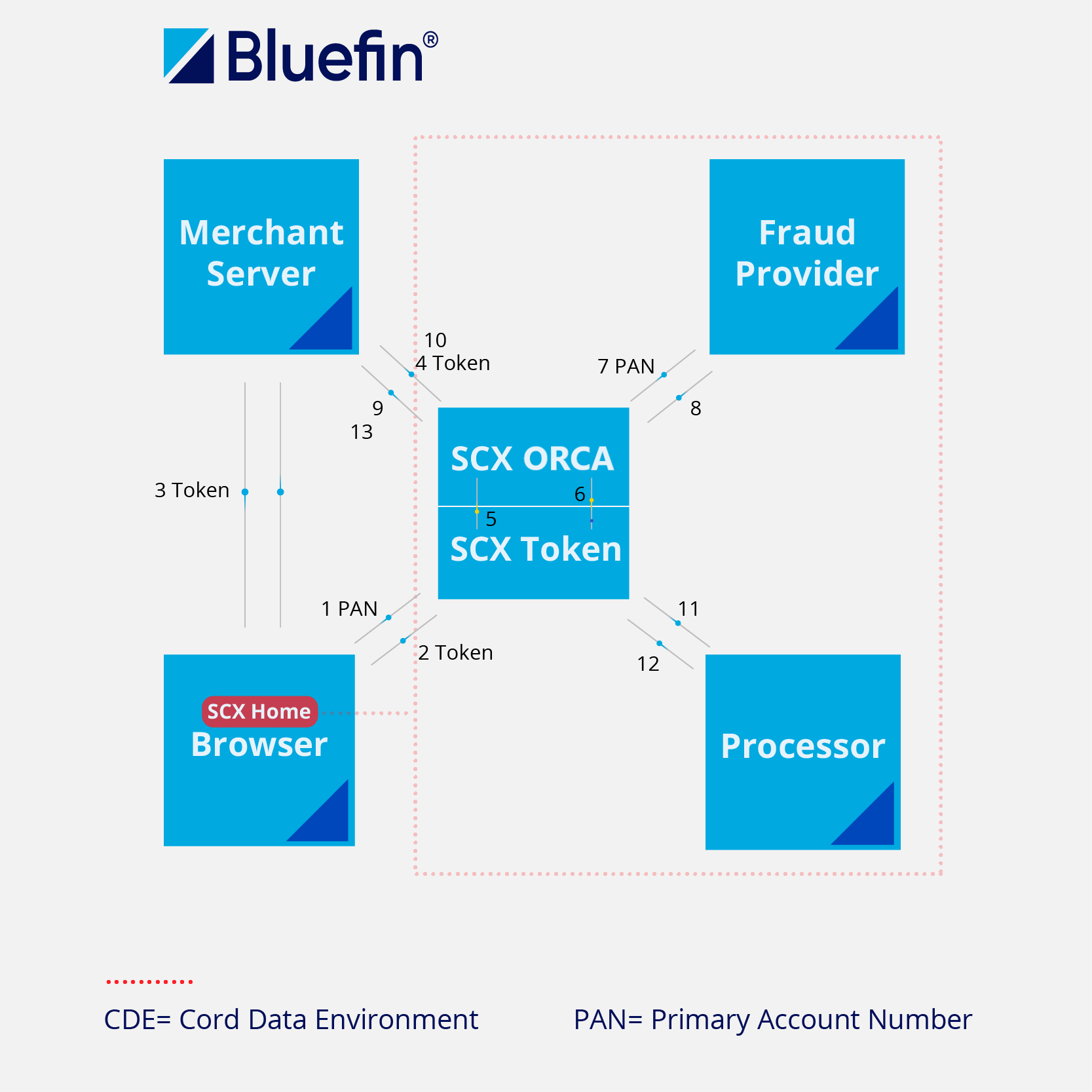
Using Fraud Services with ShieldConex® Orchestration
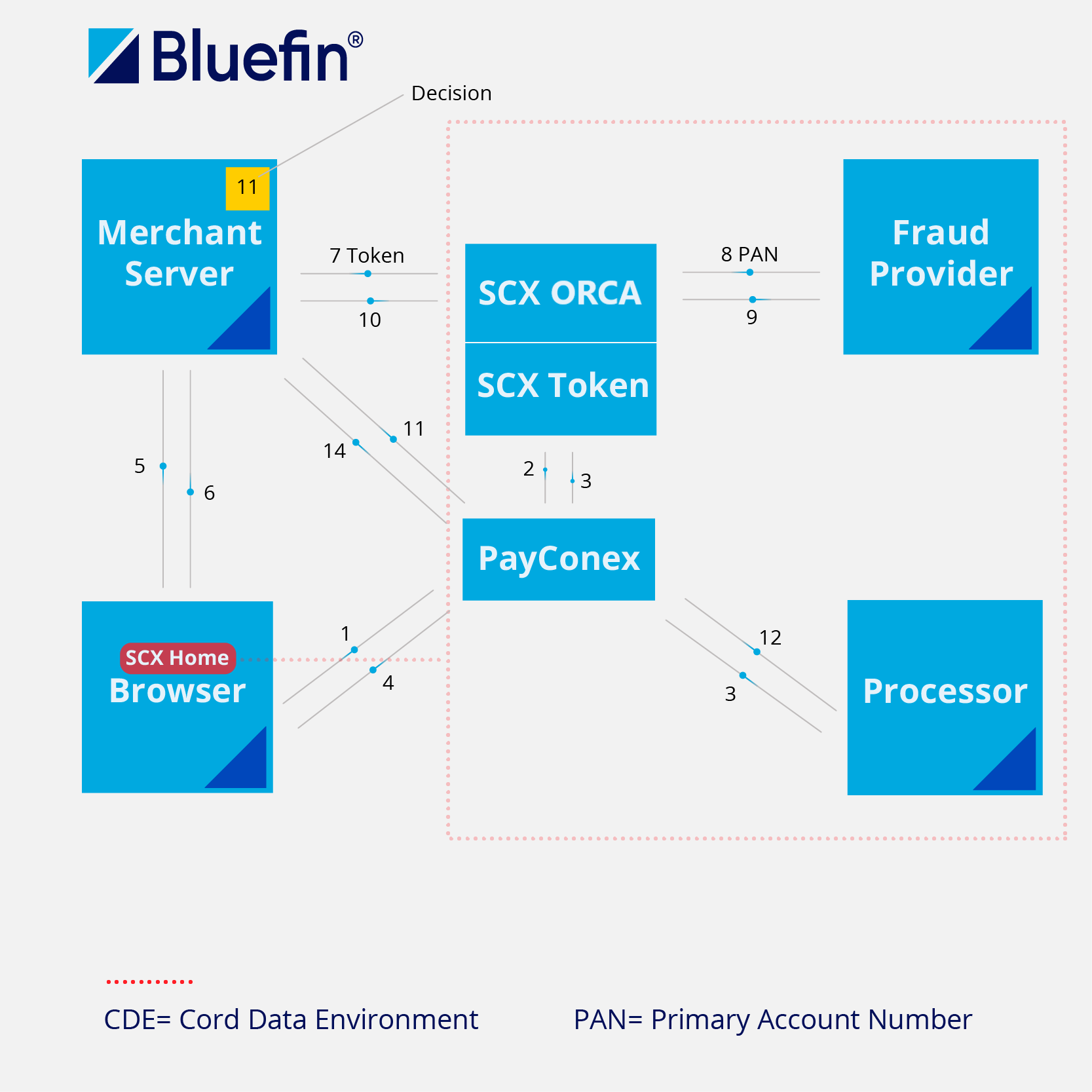
Using Fraud Services and PayConex™ with ShieldConex® Orchestration
Benefits:
- Direct fraud integration without handling CHD/SAD in your environment.
- Flexibility around the following:
- Fraud providers
- Fraud provider schemas
- Handling fraud scores
- Pause transactions
- Combine fraud score with other data before making decisions
Support
Looking for customer or technical support? Click here to contact our support team with questions about billing, devices, gateway issues, PCI inquiries, or other current customer-related questions.
Updated 6 days ago
We recommend checking out the Quickstart Guide in the Getting Started page before moving on to the Example Use Case.
