References
Supported Payload Formats
JSONXMLUrl Form Encoded(API Examples | URL Form Encoded Payload)Url Query String(API Examples | URL Queries)
Dynamic URL Path Support
ShieldConex ORCA API supports a configurable HTTP header that allows clients to dynamically set the URL path used in downstream calls.
Flexible routing for specific API operations
Nowadays, it is common for payment processor APIs to structure their endpoint paths according to specific operations. For example, a payment processor API may expose separate routes for transaction types such as sale, authorization, refund, or similar.
For this critical use case, merchants can specify a dynamic URL path that is appended to the target destination per ORCA API call.
ORCA Configuration
{
"proxy": {
"method": "post",
"target": "https://example-payment-processor.site",
"authorization": { ... }
},
"requestActions": [
{
"type": "parser",
"authorization": {
"type": "basic",
"username": "{partnerID}",
"password": "{partnerKey}"
},
"instructions": [
{
"transformationSource": "body",
"transformationType": "jsonpath",
"transformationPath": "$.Card.Track2",
"format": "pan",
"dataType": "string",
"default": "mydefault"
}
]
}
]
}
ORCA Request Configuration
POST https://proxy{-*}.shieldconex.com/api/v1/partners/{partnerID}/configurations/{configReferenceID}
{
method: "POST",
headers: {
"orca-destination-path": "/sale-transaction",
"dpx-device-serial": "{deviceSerial}",
"dpx-device-type": "{deviceType}",
"dpx-payload": "{devicePayload}",
"Authorization": "{authKey}",
"Content-Type": "application/json",
},
body: {
"Card" : {
"Name" : "John Smith",
"Password" : "supersecret",
"Track2" : "XXXXXXXXXXXXX"
}
}
}
According to the individual ORCA API call, the ORCA dynamically modifies the target destination and forwards the payload data to
https://example-payment-processor.site/sale-transaction- being the final payment processor destination.For more API examples, refer to API Examples.
Domain Immutability
The domain always remains fixed — only the path segment can be customized.
Dynamic Path Overriding
If a path is defined both statically and dynamically, the dynamic path overrides the configuration.
For example, if the target destination for an ORCA configuration is the following:
{
"proxy": {
"method": "post",
"target": "https://example-payment-processor.site/main-payment",
"authorization": { ... }
},
...
}
With our ORCA API call defining the specific orca-destination-path, the ORCA dynamically overrides the destination path and forwards the processed data payload onto https://example-payment-processor.site/sale-transaction, leaving the domain URL untouched.
{
method: "POST",
headers: {
"orca-destination-path": "/sale-transaction",
"dpx-device-serial": "{deviceSerial}",
"dpx-device-type": "{deviceType}",
"dpx-payload": "{devicePayload}",
"Authorization": "{authKey}",
"Content-Type": "application/json",
},
body: {
"Card" : {
"Name" : "John Smith",
"Password" : "supersecret",
"Track2" : "XXXXXXXXXXXXX"
}
}
}
ORCA Configuration JSON Schema Definitions
-
proxy(object) (Required):The
proxyobject contains all the settings required by the third party endpoint andlogSettingsfor the Orchestration Logs.-
authorization(object) (Required):-
type(enum) (Required) :"passthrough" | "basic" | "hmac" | "hmac-vpc"-
see Further Information section below for description of authentication types
-
Note
The difference between the
proxy.authorizationand authorization per action is that the proxy authorization is required of the target destination(payment processor) while an action requires a partner's credentials to tokenize/decrypt. In the case of ShieldConex®, a template reference that is under a certain partner. For Decryptx® action, it must use the separate authorization (P2PE Manager credentials).Alternatively, the developer can even pass additional headers as a way of custom authorization that is accepted by the target destination (in this case, the custom header must not be named
authorization).
-
-
type: "passthrough":- The custom authorization header for the target destination.
- With
headerNameprovided, the authorization data (from it) is replaced for theAuthorizationheader and passed through as such. headerName(string) (Optional):- The key of the header that contains the authorization data for the passthrough. We strongly advise that the header name is all lowercase as the ShieldConex® ORCA API forwards the header names in lowercase according to the RFC 9110 HTTP Specification.
-
type: "basic":-
For example, this is what ShieldConex ORCA forwards to the target destination.
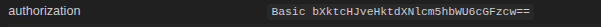
Proxy Auth Basic
-
username(string) (Required):- User name of Base64-decoded token for the target destination/payment processor
-
password(string) (Required):- Password of Base64-decoded token for the target destination/payment processor
-
-
type: "hmac":-
The ShieldConex ORCA also automates the HMAC authentication for the target destination/payment processor by generating and combining nonce, timestamp, and content hash based on the
usernameandsecretspecified forproxy.authorizationof an ORCA configuration.- If you are new to HMAC Authentication, refer to our HMAC Authentication Guide.
-
For example, this is what ShieldConex ORCA forwards to the target destination.
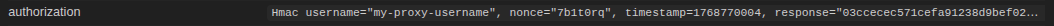
Proxy Auth HMAC
-
username(string) (Required):- User name for HMAC header for the target destination.
-
secret(string) (Required):- Required secret value in order to construct the HMAC authentication header.
-
-
type: "hmac-vpc":- This property is used to authorize requests to the Cybersource REST API (which connects to the VPC Gateway), enabling secure communication with Visa APIs. For a separate ORCA section on this, check out Proxy Authorization | Visa HMAC-based Proxy Authentication.
keyId(string) (Required):- The key identifier of a Shared Secret Key Pair created from the Cybersource Business Center. See Cybersource | Developer | Create a Shared Secret Key Pair.
secretKey(string) (Required):- The secret key of a Shared Secret Key Pair created from the Cybersource Business Center. See Cybersource | Developer | Create a Shared Secret Key Pair.
signableHeaders(array<string>) (Required):- All the Cybersource REST API header fields that must be included in the signature hash. See Cybersource | Developer | Generate the Signature Hash.
-
-
method(enum) (Required):"get" | "post" | "put" | "patch" | "delete"- Supported HTTP method for the Orchestration API
-
target(string) (Required):- The target URL or IP Address (the Payment Processor). May include the port.
-
logSettings(object) (Optional):-
An object containing all the logging rules for this type of API call. This includes the request and response masks that go out to the proxy/target destination.
-
As mentioned above, these
logSettingsare specified for the Orchestration Logs. -
requestMasks(array):-
An array containing objects that specifiy the location of data within the incoming payload that should be masked. The object will also contain the masking pattern.
-
transformationSource(enum) (Required):"body | header | query"- The source of the data. The request or the response (responseMasks)
-
transformationType(enum) (Required):"jsonpath" | "xpath" | "key" | "regex"- Specifies the type of transformation, both masking and instructions support it
- Using either
"jsonpath" | "xpath" | "regex"requirestransformationSourceto be"body" - Using
"key"requirestransformationSourceto be"header" | "query"
-
transformationPath(string) (Required):- The element within the payload to mask
jsonpathe.g."$.Card.Track2"xpathe.g."//Card/Password/text()"regexe.g.".*"- the regular expression to the path to mask - this masks everything in the payload for examplekeye.g."track2"
For more on
xpathandjsonpath, refer to JSONPath and XPath. -
pattern(enum) (Required):- See Further Information section below for Supported Masking Patterns.
-
-
responseMasks(array):- Based on the
transformationPaths,responseMaskstake the response of the target URL and masks it for the Orchestration Logs since the response data from the target URL is reinserted and proxied back to the source/client. These are configured in the same way asrequestMasks. See requestMasks above.
- Based on the
-
-
-
requestActions(array) (Required):Note
The
requestActionsobject contains a list of actions to be executed as part of the request. These actions can be driven by either ShieldConex® or Decryptx®. It is possible to have multiple actions in a row as long as your ORCA configurationtransformationPaths don't conflict and are well-organized.-
type(enum) (Required):"parser" | "shieldconex"- Specifies the type of action, which can be either
"parser"or"shieldconex"
- Specifies the type of action, which can be either
-
authorization(object) (Required):-
type(enum) (Required) :"passthrough" | "basic" | "hmac" -
passthrough:- Passes on the ShieldConex® partner credentials. For the exception of
type: "parser", see Authentication Types. headerName(string) (Optional):- The key of the header that contains the authorization data for the passthrough. We strongly advise that the header name is all lowercase as the ShieldConex® ORCA API forwards the header names in lowercase according to the RFC 9110 HTTP Specification.
- Passes on the ShieldConex® partner credentials. For the exception of
-
basic:username(string) (Required):partnerID- ID provided by Bluefin for access to the ShieldConex®/Decryptx® API
password(string) (Required):partnerKey- API Key provided by Bluefin for access to the ShieldConex®/Decryptx® API. This value can be changed on request from the partner or by the partner via the ShieldConex® Manager
-
hmac:-
username(string) (Required):partnerID- ID provided by Bluefin for access to the ShieldConex®/Decryptx® API
-
secret(string) (Required):-
Hmac Secret- provided by Bluefin from ShieldConex®/Decryptx® Partner Account. It would require setting API Security to Hmac and Bluefin would give you the Hmac Secret and Base64 Decoded Key. It is the Base64 Decoded Key that is used by this field.
API Security - HMAC
Setting API Security to Hmac affects all the ORCA configurations under the specific Partner Account.
-
-
-
-
logSettings(object) (Optional):-
An object containing all the logging rules for the API call of an action. This includes the request and response masks that are used to mask ShieldConex® and Decryptx® operations.
-
As mentioned above, these
logSettingsare specified for the Orchestration Logs. -
Warning
For an action, this setting is optional and is intended for merchants/developers who already have a background in ShieldConex® and Decryptx® API services in order to properly set up the masking for maximum security according to their needs and the particular way they would like to adapt their logs. For that reason, by default an ORCA configuration masks all the sensitive data that is processed by these services.
Before using this feature, we recommend consulting with our Bluefin Technical Team.
-
requestMasks(array):-
An array containing objects that specifiy the location of data within the incoming payload that should be masked. The object will also contain the masking pattern.
-
transformationSource(enum) (Required):"body | header | query"- The source of the data. The request or the response (responseMasks)
-
transformationType(enum) (Required):"jsonpath" | "xpath" | "key" | "regex"- Specifies the type of transformation, both masking and instructions support it
- Using either
"jsonpath" | "xpath" | "regex"requirestransformationSourceto be"body" - Using
"key"requirestransformationSourceto be"header" | "query"
-
transformationPath(string) (Required):- The element within the payload to mask
jsonpathe.g."$.Card.Track2"xpathe.g."//Card/Password/text()"regexe.g.".*"- the regular expression to the path to mask - this masks everything in the payload for examplekeye.g."track2"
For more on
xpathandjsonpath, refer to JSONPath and XPath. -
pattern(enum) (Required):- See Further Information section below for Supported Masking Patterns.
-
-
responseMasks(array):- Based on the
transformationPaths,responseMaskstake the response of the target URL and masks it for the Orchestration Logs since the response data from the target URL is reinserted and proxied back to the source/client. These are configured in the same way asrequestMasks. See requestMasks above.
- Based on the
-
-
type: "shieldconex"-
method(enum) (Required):"tokenize" | "detokenize"- This setting is required when the
typeof service isshieldconex
- This setting is required when the
-
templateRef(string) (Required):- Template Reference. This is the unique alphanumeric string that is used to identify a template. The templateRef is created within the ShieldConex® Manager and can be found within the template details page of any template within the ShieldConex® Manager.
-
instructions(array) (Required):-
An array of substitution configurations to apply to the incoming payload. Each entry will have a location for the substitution and the ShieldConex® token to use.
-
transformationSource(enum) (Required):"body | header | query"- The source of the data. The request or the response
-
transformationType(enum) (Required):"jsonpath" | "xpath" | "key" | "regex"- Specifies the type of transformation, both masking and instructions support it
- Using either
"jsonpath" | "xpath" | "regex"requirestransformationSourceto be"body" - Using
"key"requirestransformationSourceto be"header" | "query"
-
transformationPath(string) (Required):- The element within the payload to replace with the tokenized/detokenized value. The pattern used is determined by the
transformationType. xpathe.g."//Card/Password/text()"jsonpathe.g."$.Card.Track2"regexe.g.".*"- the regular expression to the path to mask - this masks everything in the payload for examplekeye.g."track2"
For more on
xpathandjsonpath, refer to JSONPath and XPath. - The element within the payload to replace with the tokenized/detokenized value. The pattern used is determined by the
-
fieldName(string) (Required):-
The system name of the ShieldConex® template field to which the value is mapped for tokenization/detokenization
Note
This field name is taken from the template created via the ShieldConex® Template Manager
e.g.
"scx_token_card_number"
-
-
instructionType(string) (Optional) (default:"substitution"):substitution- tokenize or detokenize information and replace the source data in the payload, this is the default setting when the variable is not defined in the configurationpassthrough- tokenize without replacing any data in the payload and retrieve tokens asynchronously using the BFID returned in the response of the ORCA API request
-
-
-
type: "parser":-
method(string) (Optional) (default:"decrypt"):- Decryptx® Parser type of action.
-
clientId(string) (Optional):- Identifier for partner client to which this device belongs. This value is configured by the partner when the device is provisioned and is optional. This parameter provides an additional level of uniqueness in case device serial numbers are not unique between manufacturers. It also provides a more detailed level of reporting as API usage can be reported to the Client level. All devices provisioned for a partner must have a unique combination of Serial Number and Client. If a partner does not wish to use a client identifier, all devices provisioned for that partner must have a unique Serial Number.
-
deviceType(string) (Optional):- The type of terminal that generated the payload to be decrypted. The value must be one of the following:
generic,idtech,ingenico-ra1,ingenico-rba,miura,prima,verifone,wisepad, orwisepad2.
- The type of terminal that generated the payload to be decrypted. The value must be one of the following:
-
serialLocation(object) (Optional):-
Specifies the location for the serial number of the device that generated the payload. Even though the serial is usually extracted from the device payload itself, this allows for further customization as the serial number (as human-readable format) may be extracted from the body, header, or query of the ORCA API request as the following settings indicate. Compare to ORCA Decryptx® Request Configuration.
-
transformationSource(enum) (Required):"body | header | query"- The source of the data. The request or the response
-
transformationType(enum) (Required):"jsonpath" | "xpath" | "key" | "regex"- Specifies the type of transformation, both masking and instructions support it
- Using either
"jsonpath" | "xpath" | "regex"requirestransformationSourceto be"body" - Using
"key"requirestransformationSourceto be"header" | "query"
-
transformationPath(string) (Required):- The element within the payload to replace with the decrypted serial value. The pattern used is determined by the
transformationType. xpathe.g."//Card/Password/text()"jsonpathe.g."$.Card.Track2"regexe.g.".*"- the regular expression to the path to mask - this masks everything in the payload for examplekeye.g."track2"
For more on
xpathandjsonpath, refer to JSONPath and XPath. - The element within the payload to replace with the decrypted serial value. The pattern used is determined by the
-
-
instructions(array) (Required):-
An array of polyfill configurations to apply to the incoming payload. Each entry should include:
- Location: Location for the polyfill within the payload.
- Format: See Further Information section below for format options.
-
transformationSource(enum) (Required):"body | header | query"- The source of the data. The request or the response
-
transformationType(enum) (Required):"jsonpath" | "xpath" | "key" | "regex"- Specifies the type of transformation, both masking and instructions support it
- Using either
"jsonpath" | "xpath" | "regex"requirestransformationSourceto be"body" - Using
"key"requirestransformationSourceto be"header" | "query"
-
transformationPath(string) (Required):- The element within the payload to replace with the decrypted value. The pattern used is determined by the
transformationType. xpathe.g."//Card/Password/text()"jsonpathe.g."$.Card.Track2"regexe.g.".*"- the regular expression to the path to mask - this masks everything in the payload for examplekeye.g."track2"
For more on
xpathandjsonpath, refer to JSONPath and XPath. - The element within the payload to replace with the decrypted value. The pattern used is determined by the
-
dataType(enum) (Required):"string" | "number" | "boolean"- The datatype to use when outputting the data.
-
default(string | null):- An optional value that can be set if a value is not present in the decrypted payload.
-
format(enum) (Required):-
The format to use when substituting elements within the payload. This option also indicates the type of data that should be extracted from the Parser response for substitution.
-
Also see Decryptx® Parser API Reference.
-
-
See Supported PolyfillFormat Options below for format options.
-
-
instructionType(string) (Optional) (default:"substitution"):substitution- decrypt information and replace the source data in the payload, this is the default setting when this option is not defined in the configuration
-
-
-
-
responseActions(array) (Optional):
Note
The
responseActionsobject is executed after the downstream response is received and before returning to the client, tokenizing values returned by the payment processor.For more details and its usage, refer to ShieldConex | ORCA Request and Response Actions.
-
type(enum) (Required):"shieldconex"- Specifies the type of action, which can only be
"shieldconex"for a response action.
- Specifies the type of action, which can only be
-
authorization(object) (Required):-
type(enum) (Required) :"passthrough" | "basic" | "hmac" -
passthrough:- Passes on the ShieldConex® partner credentials.
headerName(string) (Optional):- The key of the header that contains the authorization data for the passthrough. We strongly advise that the header name is all lowercase as the ShieldConex® ORCA API forwards the header names in lowercase according to the RFC 9110 HTTP Specification.
-
basic:username(string) (Required):partnerID- ID provided by Bluefin for access to the ShieldConex® API
password(string) (Required):partnerKey- API Key provided by Bluefin for access to the ShieldConex® API. This value can be changed on request from the partner or by the partner via the ShieldConex® Manager
-
hmac:-
username(string) (Required):partnerID- ID provided by Bluefin for access to the ShieldConex® API
-
secret(string) (Required):-
Hmac Secret- provided by Bluefin from ShieldConex® Partner Account. It would require setting API Security to Hmac and Bluefin would give you the Hmac Secret and Base64 Decoded Key. It is the Base64 Decoded Key that is used by this field.
API Security - HMAC
Setting API Security to Hmac affects all the ORCA configurations under the specific Partner Account.
-
-
-
-
logSettings(object) (Optional):-
An object containing all the logging rules for the API call of an action. This includes the request and response masks that are used to mask ShieldConex® and Decryptx® operations.
-
As mentioned above, these
logSettingsare specified for the Orchestration Logs. -
requestMasks(array):-
An array containing objects that specifiy the location of data within the incoming payload that should be masked. The object will also contain the masking pattern.
-
transformationSource(enum) (Required):"body | header | query"- The source of the data. The request or the response (responseMasks)
-
transformationType(enum) (Required):"jsonpath" | "xpath" | "key" | "regex"- Specifies the type of transformation, both masking and instructions support it
- Using either
"jsonpath" | "xpath" | "regex"requirestransformationSourceto be"body" - Using
"key"requirestransformationSourceto be"header" | "query"
-
transformationPath(string) (Required):- The element within the payload to mask
jsonpathe.g."$.Card.Track2"xpathe.g."//Card/Password/text()"regexe.g.".*"- the regular expression to the path to mask - this masks everything in the payload for examplekeye.g."track2"
For more on
xpathandjsonpath, refer to JSONPath and XPath. -
pattern(enum) (Required):- See Further Information section below for Supported Masking Patterns.
-
-
responseMasks(array):- Based on the
transformationPaths,responseMaskstake the response of the target URL and masks it for the Orchestration Logs since the response data from the target URL is reinserted and proxied back to the source/client. These are configured in the same way asrequestMasks. See requestMasks above.
- Based on the
-
-
type: "shieldconex"-
method(enum) (Required):"tokenize"- This setting is required when the
typeof service isshieldconex
- This setting is required when the
-
templateRef(string) (Required):- Template Reference. This is the unique alphanumeric string that is used to identify a template. The templateRef is created within the ShieldConex® Manager and can be found within the template details page of any template within the ShieldConex® Manager.
-
instructions(array) (Required):-
An array of substitution configurations to apply to the incoming payload. Each entry will have a location for the substitution and the ShieldConex® token to use.
-
transformationSource(enum) (Required):"body | header | query"- The source of the data. The request or the response
-
transformationType(enum) (Required):"jsonpath" | "xpath" | "key" | "regex"- Specifies the type of transformation, both masking and instructions support it
- Using either
"jsonpath" | "xpath" | "regex"requirestransformationSourceto be"body" - Using
"key"requirestransformationSourceto be"header" | "query"
-
transformationPath(string) (Required):- The element within the payload to replace with the tokenized value. The pattern used is determined by the
transformationType. xpathe.g."//Card/Password/text()"jsonpathe.g."$.Card.Track2"regexe.g.".*"- the regular expression to the path to mask - this masks everything in the payload for examplekeye.g."track2"
For more on
xpathandjsonpath, refer to JSONPath and XPath. - The element within the payload to replace with the tokenized value. The pattern used is determined by the
-
fieldName(string) (Required):-
The system name of the ShieldConex® template field to which the value is mapped for tokenization/detokenization
Note
This field name is taken from the template created via the ShieldConex® Template Manager
e.g.
"scx_token_card_number"
-
-
instructionType(string) (Optional) (default:"substitution"):substitution- tokenize information and replace the source data in the payload, this is the default setting when the variable is not defined in the configurationpassthrough- tokenize without replacing any data in the payload and retrieve tokens asynchronously using the BFID returned in the response of the ORCA API request
-
-
Further Information
Authentication Types
-
passthrough- The original incoming request contains the authorization either as a header or in the body. This option does not authenticate requests itself but forwards them to a back-end service that handles the authentication. Either way, if the authentication headers are invalid, the request will be rejected.-
Note
Using
passthroughfor aparseraction will result inAuthentication requiredin the Orchestration Logs since it passes ShieldConex® partner credentials from the request as opposed to the Decryptx® credentials. For the reason outlined, it is fine to usepassthroughfor ashieldconexaction. However, it is possible to specifyheaderNameas that header will be extracted for that action. For example,{ ... "requestActions": [ { "type": "parser", "authorization": { "type": "passthrough", "headerName": "my-decryptx-header" }, ... ], ... }
-
-
basic- Add a basic auth header (config to be stored on server) -
hmac- add a hmac auth header (config to be stored on server)
Supported Masking Patterns
Masks affect Portal Orchestration Logs.
all- The entire value will be masked.fourPlainFourMasked- Every four characters are masked.allButFirstSixLastFour- The middle is masked but the first six and last four characters are not.allButFirstOneLastFour- The middle is masked but the first character as well as the last four characters are not.
Supported PolyfillFormat Options
-
rawTrack2- The complete track2 payload containing the start and end sentinels. e.g.;4124939999999990=2212101123456789?; -
track2- Defined as PAN=EXP[CVV][serviceCode]?LRC, and is equal to rawTrack2 without the sentinels e.g.4124939999999990=2212101123456789 -
track2equivalentLower- Track2 equivalent with a lower case d e.g.4124939999999990d2212101123456789 -
track2equivalentUpper- Track2 equivalent with a lower case d e.g.4124939999999990D2212101123456789 -
rawTrack1- Track1 with the sentinels e.g.%B4124939999999990^TEST/BLUEFIN^2212101123456789? -
track1- Track1 without the sentinels e.g.B4124939999999990^TEST/BLUEFIN^2212101123456789 -
pan- The card number e.g.4124939999999990 -
expiry- The expiry month and year (MMYYformat) e.g.1222 -
expiryMonth- The expiry month e.g.12 -
expiryYear- The expiry year e.g.22 -
fullYear- The full expiry year e.g.2022 -
expiryRaw- The expiry month and year (YYMMformat) e.g.2212. This enhances compatibility with specific ISO payment processors format -
cvv- The 3-character CVV (captured during keyed transactions on idtech). -
discretionary- The track's discretionary data e.g.123456789 -
firstName- The cardholder's first name e.g.Jane -
firstNameAndSurname- The cardholder's complete name. e.g.Jane Smith -
rawName- The cardholder's name as it appears on the track. e.g.TEST/BLUEFIN
Fundamental Request Configuration Header Detail
ORCA Decryptx® Request Configuration
headers: {
"dpx-device-serial": "<deviceSerial>",
"dpx-device-type": "<deviceType>",
"dpx-payload": "<devicePayload>",
"dpx-ksn": "<deviceKSN>",
"Authorization": "<authKey>",
"Content-Type": "application/json"
},
body: "{ ... }"
Header Parameters
| Parameter | Description |
|---|---|
deviceSerial | The serial number of the device used to process the transaction. This field is optional as the decryption is optional to begin with, and even if Decryptx® is used, the device payload might contain the serial number. |
deviceType | The type of device used to process the transaction. This field is optional as the decryption is optional. |
devicePayload | The device payload to be decrypted. This field is optional as the decryption is optional. |
ksn (optional) | The key sequence number (KSN) used to encrypt the payload. This parameter is not required when decrypting payloads from the IDTech or Ingenico devices as they embed the KSN in their payloads. |
authKey | Authentication token. See ORCA API Authentication. |
Content-Type | Content Encoding: "application/json" | "application/xml" |
For more information, see Decryptx Parser | API Reference.
ORCA ShieldConex® Detokenization Request Configuration
headers: {
"Authorization": "<authKey>",
"scx-bfid": "<bfid>",
"Content-Type": "application/json"
},
body: "{ ... }"
Header Parameters
| Parameter | Description |
|---|---|
Authorization | Authentication token. See ORCA API Authentication. |
scx-bfid | The ShieldConex® BFID for payloads that contain ShieldConex® tokens for detokenization. |
Content-Type | Content Encoding: "application/json" | "application/xml" |
Passing Additional Headers
If there are additional headers that you would like to pass onto the target destination (payment processor), the ShieldConex® Orchestration API makes it available so since additional headers are ignored as long as they are not part of the ORCA configuration. See ORCA Configuration with Headers.
For example, this custom-header-test is passed onto the target destination.
headers: {
"Authorization": "<authKey>",
"scx-bfid": "<bfid>",
"custom-header-test": "yes",
"Content-Type": "application/json"
},
body: "{ ... }"
Responses and Errors
Below is the error response in JSON format.
{
"success": false,
"code" : 8001,
"message": "Server error."
}
HTTP Responses
-
200 (Success)
-
Result(object) -
a place to capture all the response data
The body of the success response is usually dictated by the target URL.
-
-
400 (Bad Request)
-
success(boolean) (Required)- True for successful API calls, false for failed
-
message(string) (Required)- A human readable error message
-
code(int32) (Required)- Pragmatic code for specific failure reason.
-
-
500 (Internal Server Error)
For a more detailed response, we recommend checking out the Orchestration Logs in the ShieldConex® Manager.
-
success(boolean) (Required)- True for successful API calls, false for failed
-
message(string) (Required)- A human readable error message
-
code(int32) (Required)- Pragmatic code for specific failure reason.
-
Error Codes
Below are the possible error codes returned by a call to the ShieldConex® Orchestration API.
| Error Code | HTTP Response | Description |
|---|---|---|
8001 | 500 | Internal Server Error/Unexpected Error |
8003 | 401 | Authentication Error |
8004 | 403 | Permission Denied Error |
Updated about 1 month ago
