ShieldConex® Network Tokens
ShieldConex Network Tokens Documentation and API Examples
Large Enterprise Merchants and Payment Facilitators
ShieldConex® Orchestration and Network Token Service are common for large ISVs.
For merchants with smaller businesses, we recommend using the PayConex™ Suite of APIs.
Overview
Network tokens are:
- Digital substitutes for sensitive card information used in payment processing. They enhance security by replacing card details with unique identifiers, reducing the risk of data breaches. Benefits include increased transaction security, reduced fraud, and streamlined online payment experiences.
- Used in mobile wallets, e-commerce transactions, and recurring payments, ensuring that sensitive card data is never exposed during transactions, thereby maintaining privacy and compliance with security standards.
- Able to receive updates from the card issuer, such as card reissues or expiration date changes, without requiring the cardholder to update their details. Payment Service Provider does not need account updater service for a network token. In other words, network tokens basically do not expire this way even if the cardholder changes the card information.
Network Token Support
To date, network tokens are used in roughly 30% of Visa and Mastercard transactions. ShieldConex combines Network Tokens with its own tokenization solution, allowing merchants to generate the most cost-effective token for each transaction—whether for security, routing flexibility, or downstream savings.
Bluefin's ShieldConex®
ShieldConex® uses a system called vaultless tokenization.
For more information, see ShieldConex | Tokenization Explained and ShieldConex® Orchestration.
API Authentication
To authenticate with the ShieldConex API, please refer to the API Authentication.
API Reference
For the comprehensive API reference including body requests and responses, refer to ShieldConex API | Network Token Bundle.
Bluefin Network Token Service
Bluefin ShieldConex® incorporates its Network Token Service, by providing a set of REST API endpoints that manage network tokens, enhancing our tokenization services, simplifying the integration process, and most importantly - offering additional choices to the merchant.
Merchants can use these endpoints either through individual Network Token API calls or ShieldConex Tokenization.
Generating Network Tokens via ShieldConex Tokenization allows merchants to use ShieldConex payment tokens at the same time, which is especially useful if they switch to a different payment processor.
This approach streamlines the process, as Bluefin's Integration team handles the technical details, integration, and delivers a ready-to-use solution.
In essence, ShieldConex Network Token Service handles the tokens on the merchant's behalf.
This can be illustrated in the following diagram:
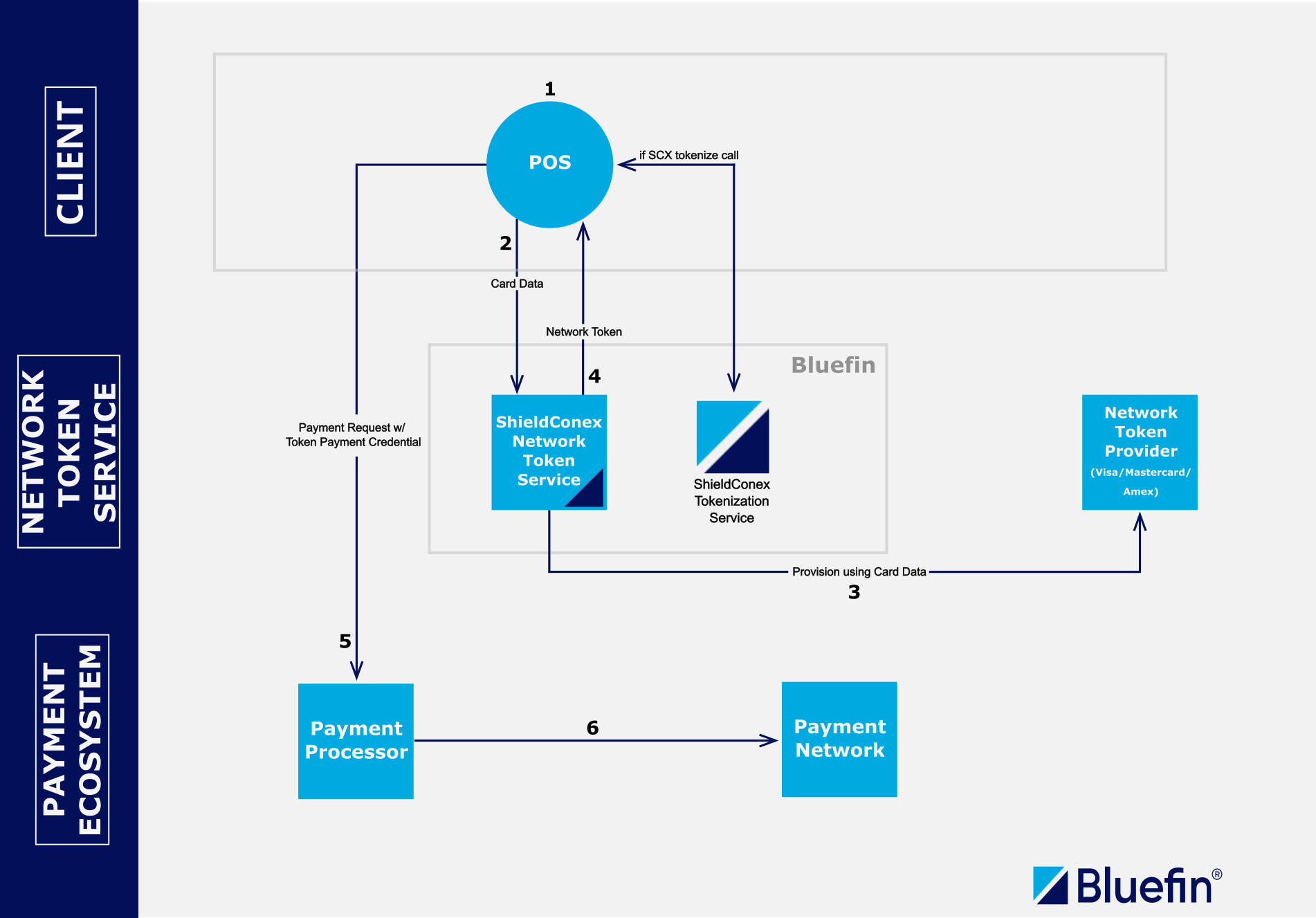
ShieldConex® & Network Token Service Workflow
- The customer makes a purchase at the Point Of Sale systems maintained by the merchant. This can be a website, payment application, or similar.
- The sensitive card data is sent to the ShieldConex Network Token Service to create a token.
- During this step, the SCX tokenize call can be made so that the merchant also has ShieldConex tokens at their disposal and use ShieldConex ORCA during the step 5 in the diagram given that a certain payment processor does not support network tokens. For more details, see Overview | Network Token Support.
- Then, the Network Token Service provisions the token with Network Token Providers based on the card issuer. This token is essentially stored/vaulted for subsequent transactions - be it CITs or MITs.
- The network token is returned to the POS for payment processing where the merchant gets the payment credentials with the network token identifier.
- Payment Request with the network token payment credentials is made to the designated payment processor.
- The network token and cryptogram are transmitted across the payment ecosystem.
Provision a Token
In order to use a token in a payment, provisioning the token is required with the
networkTokenStateofACTIVE.After provisioning a network token through the Network Token Provider, the merchant can use the network token for future transactions. Depending on the card issuer, the Network Token Provider can be Visa, Mastercard, or Amex.
Provisioning a network token involves requesting from a card network, like Visa or Mastercard, to generate a unique token representing a card's Primary Account Number (PAN). This token is then used in subsequent transactions instead of the actual PAN, enhancing security.
Integration Options
There are two ways the merchant can integrate with the Network Tokens.
-
Template Configuration (as a field of the ShieldConex iFrame)
- Card Information or Custom Field option
-
ShieldConex REST API
- Standalone NT API calls for managing Network Tokens
- Recommended Approach
- ShieldConex Tokenization & Network Tokens with Template Configuration in the case of switching to a different payment processor with ShieldConex tokens. ShieldConex tokens work with any processor, so there is no exporting and importing tokens when changing processors.
- For more information, also see ShieldConex | Tokenization Explained and ShieldConex® Orchestration.
- Widely adopted, Network Tokens enable secure processing of card-not-present (CNP) payments with the majority of payment processors.
Environment URLs
There are two ShieldConex environments each with their own URL.
| Environment Name | Endpoint | Description |
|---|---|---|
| Certification (Testing) Environment | https://secure-cert.shieldconex.com | Use this environment for development and testing. |
| Production (Live) Environment: | https://secure.shieldconex.com | Use this environment for live requests. |
All requests must be made over HTTPS for security. Append the endpoints described below to the appropriate base URL depending on whether you are testing or running in production.
For example, this is the full URL for creating a network token in the certification environment:
https://secure-cert.shieldconex.com/api/network-token-bundle
Certifying your Integration
All preliminary development must be conducted and tested within the certification environment.
API Endpoint Overview
To use network tokens as a standalone solution, ShieldConex API offers the following endpoints.
| Endpoint | HTTP Method | Description |
|---|---|---|
/api/network-token-bundle | POST | Both create and provision a token. |
/api/network-token-bundle/{networkTokenBundleId} | GET | Get Network Token Bundle. |
/api/network-token-bundle/{networkTokenBundleId}/payment-credentials | GET | Get Payment Credentials used for secure payment processing. This endpoint is required to process a CIT with the cryptogram where subsequent MITs reuse all the other fields from the response (expect for the cryptogram). That is to say, the cryptogram is required to process a CIT. See Get Payment Credentials. |
/api/network-token-bundle/{networkTokenBundleId} | DELETE | Delete a network token bundle. |
Terminology: Network Token Bundle
In ShieldConex API, network tokens are treated as the Network Token Bundle schema, which represents a comprehensive data structure used to process payments with network tokens.
If you want to use network tokens as part of ShieldConex solution, use the following endpoints.
Recommended Approach
ShieldConex Tokenization & Network Tokens is the recommended approach.
| Endpoint | HTTP Method | Description |
|---|---|---|
/api/tokenization/tokenize | POST | Tokenize the card data via ShieldConex with both creating and provisioning a network token. |
/api/tokenization/detokenize | POST | Detokenize the card data via ShieldConex, and get payment credentials with the cryptogram for a CIT. See the /payment-credentials endpoint above. |
Note
If Creating a Network Token fails during the tokenization call, the ShieldConex tokens are included regardless where the
networkTokenBundleis dropped, as mentioned below.
Test Card Numbers
While you are certifying our ShieldConex Network Token Integration, use one of the following test cards based on the Network Token Provider (Card Brand).
Successful Network Token Provisioning
Use these test card numbers to successfully provision network tokens.
For Mastercard and Visa cards, replace the X in the card number with 0. For Mastercard cards, you can use any future date for the expiration date.
| Card Brand | Number | Expiration Date | CVV |
|---|---|---|---|
| American Express | Any | Any | Any |
| Mastercard | 512X342233150747 | Any | Any |
| Mastercard | 512X343287499758 | Any | Any |
| Mastercard | 51203501XXX64594 | Any | Any |
| Visa | 46229431231XX639 | 12/26 | 242 |
| Visa | 46229431231XX647 | 12/26 | 749 |
| Visa | 46229431231XX654 | 12/26 | 972 |
| Visa | 46229431231XX662 | 12/26 | 344 |
| Visa | 46229431231XX67X | 12/26 | 306 |
| Visa | 46229431231XX688 | 12/26 | 065 |
| Visa | 46229431231XX696 | 12/26 | 264 |
Unsuccessful Network Token Provisioning
Use these test card numbers to test unsuccessful provisioning of network tokens.
For American Express cards, replace the X in the PAN with a 0. For Visa cards, replace the X in the PAN with any number. You can use any future date for the expiration date.
| Card Brand | PAN | Expiration Date | CVV | Failure Reason |
|---|---|---|---|---|
| American Express | 370000000XXXX28 | Any | Any | CARD_NOT_ELIGIBLE |
| American Express | 3700000000XXXX2 | Any | Any | DECLINED |
| American Express | 37000000XXXX119 | Any | Any | SERVICE_UNAVAILABLE |
| American Express | 370000000XXXX36 | Any | Any | CARD_NOT_ALLOWED |
| Visa | 4000000011XXXXXX | Any | Any | CARD_VERIFICATION_FAILED |
| Visa | 4001770011XXXXXX | Any | Any | CARD_NOT_ELIGIBLE |
| Visa | 4010057011XXXXXX | Any | Any | CARD_NOT_ALLOWED |
| Visa | 4010057022XXXXXX | Any | Any | DECLINED |
| Visa | 4020057022XXXXXX | Any | Any | DECLINED |
| Visa | 4010057033XXXXXX | Any | Any | SERVICE_UNAVAILABLE |
| Visa | 4020057033XXXXXX | Any | Any | SERVICE_UNAVAILABLE |
| Visa | 4010057044XXXXXX | Any | Any | SYSTEM_ERROR |
| Visa | 4020057044XXXXXX | Any | Any | SYSTEM_ERROR |
| Visa | 4020057055XXXXXX | Any | Any | INVALID_REQUEST |
Template Configuration
In order to use Network Tokens as part of ShieldConex solution via either REST API or iFrame SDK, a template configuration must be referenced with FPT(Format Preserving Tokenization) + Network Tokens Data Protection Method as either Card Information or Custom Field.
Field Templates
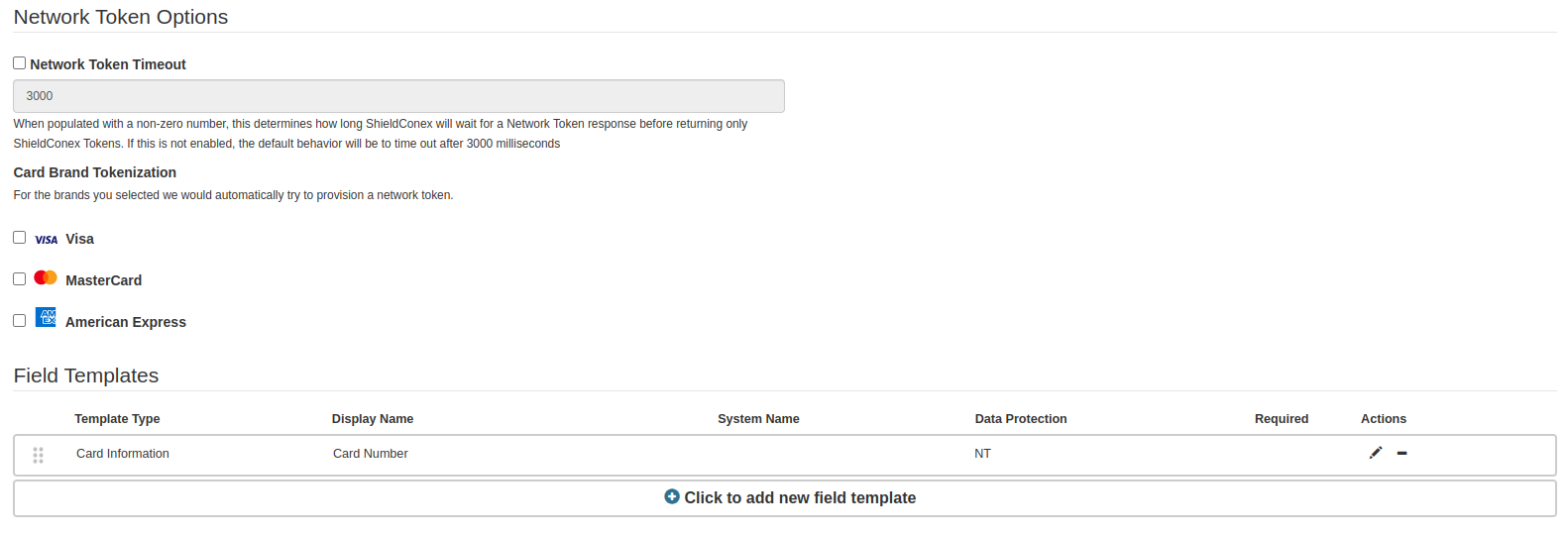
ShieldConex® Field Templates
Data Protection Method
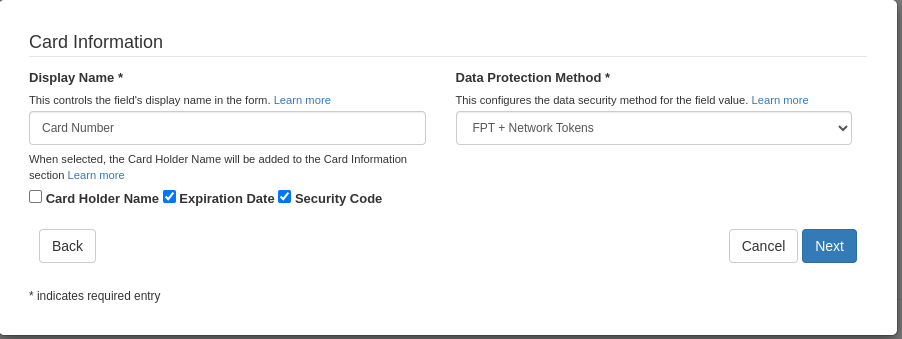
ShieldConex® Field Data Protection Method
Network Token Timeout
When a network token field is used in a ShieldConex template, there is a special setting that determines how long ShieldConex will wait for a Network Token response before returning only ShieldConex Tokens. This is due to the fact that the API call both creates and provisions a token and this timeout essentially sets a limit for those two actions.
It is also important to note that if Creating a Network Token fails, the ShieldConex tokens are included regardless where the networkTokenBundle is dropped, as mentioned below.
Card Brand Tokenization
This setting specifies the card brand the network tokens are generated for.
It is required to select card brands if you are using the network token feature. Otherwise, the networkTokenBundle is excluded for your ShieldConex Tokenization API calls altogether.
Network Token API Logs
This section of the Portal is designed to help users monitor and troubleshoot network token (NT) operations. It provides detailed logs and insights into each tokenization request, making it easier to identify and analyze failures, timeouts, or irregular behavior. This is especially useful during integration, testing, or when investigating issues with production traffic involving network tokens. These can also be used for generating reports.
These operations are referred to as Transactions including:
Create Network TokenGet Network TokenGet Payment Credentials
Here is the sample API Logs table:
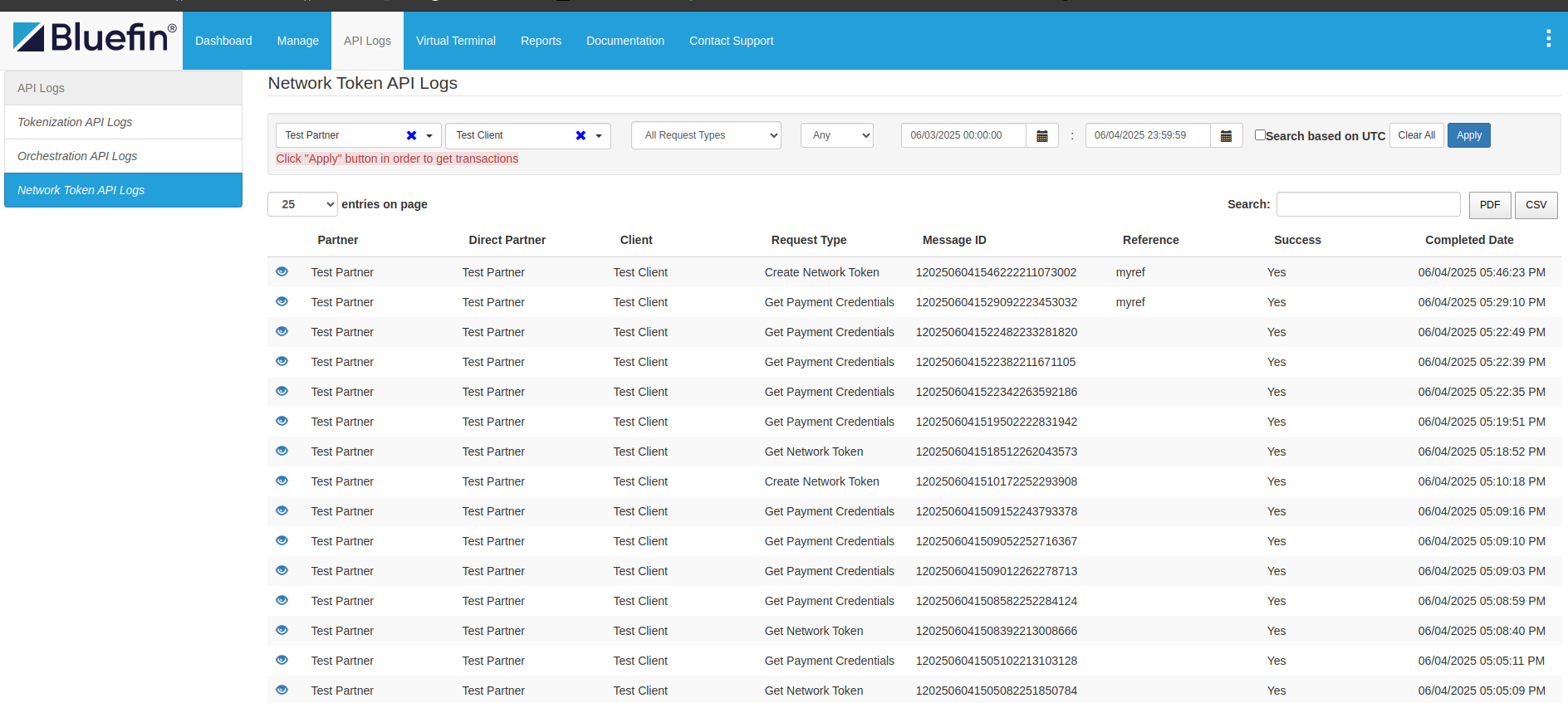
ShieldConex® Portal | Network Token API Logs
If we click on one of these items, we get the details of NT transaction like this:
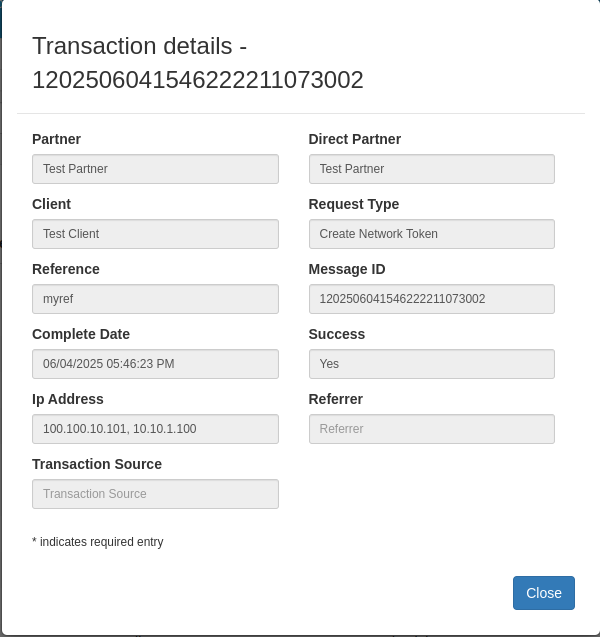
ShieldConex® Portal | Network Token API Logs | Item
Network Tokens API
scx-client-referenceThis header is required for all the following API calls in this section. This is the Client ID tied to the Partner used for API Authentication.
This set of endpoints is used if the merchant exclusively uses network tokens and opts not to receive ShieldConex tokens in the response.
Create a Network Token
Creating a network token through ShieldConex involves both creating a token and provisioning it via Network Token Provider. However, this does not retrieve the payment credentials and keeps the response data both encrypted and masked.
Existing Network Token
When creating a network token with the same card credentials, the same token id is returned with the same data, meaning that the network token already exists and is idempotent.
Network tokens can be used for these in-app payment methods:
- Android Pay
- Apple Pay
- Chase Pay
- Google Pay
- Samsung Pay
- Visa Click to Pay
These tokenized payment methods are also referred to as digital payments, digital wallets, and tokenized cards.
Request
The request body takes in the cardholder's PAN data with the expiration dates and CVV.
POST /api/network-token-bundle
{
"headers": {
"Authorization": "Basic {Base64_Encoded_API_KEY}",
"Content-Type": "application/json",
"scx-client-reference": "cl000744"
},
"body": {
"cardNumber": "4622943123155639",
"expirationMonth": "12",
"expirationYear": "2026",
"securityCode": "242"
}
}
For comprehensive descriptions of request/response parameters, see API Reference | Create Network Token.
Response
Note
In response, we get the network token entry with the data both encrypted and masked.
{
"messageId": "1202506261452471241450814",
"networkTokenBundleId": "7030070000047325639",
"networkTokenBundleState": "ACTIVE",
"networkToken": {
"networkTokenState": "ACTIVE",
"tokenizedNumber": "489537XXXXXX5690",
"expirationMonth": "12",
"expirationYear": "2026",
"type": "visa",
"card": {
"suffix": "5639",
"expirationMonth": "12",
"expirationYear": "2026"
}
},
"issuer": {
"paymentAccountReference": "V0010013025078536357001803531"
},
"metadata": {
"creator": "testbluefin_sandbox001"
}
}
Get a Network Token Bundle
This endpoint returns the corresponding network token entry with its metadata.
Note
The response data is both encrypted and masked.
Request
GET /api/network-token-bundle/{networkTokenBundleId}
{
"headers": {
"Authorization": "Basic {Base64_Encoded_API_KEY}",
"Content-Type": "application/json",
"scx-client-reference": "cl000744"
}
}
Response
{
"messageId": "1202506261454571251836563",
"networkTokenBundleId": "7030070000047325639",
"networkTokenBundleState": "ACTIVE",
"networkToken": {
"networkTokenState": "ACTIVE",
"tokenizedNumber": "489537XXXXXX5690",
"expirationMonth": "12",
"expirationYear": "2026",
"type": "visa",
"card": {
"suffix": "5639",
"expirationMonth": "12",
"expirationYear": "2026"
}
},
"issuer": {
"paymentAccountReference": "V0010013025078536357001803531"
},
"metadata": {
"creator": "testbluefin_sandbox001"
}
}
Get Payment Credentials
This endpoint is called before processing a payment to retrieve the networkTokenId and cryptogram. Additional properties of the networkToken—such as tokenizedNumber, expirationMonth, and expirationYear—are returned for secure transaction processing. It is important to note that tokenizedNumber is never the raw PAN or any sensitive data but is mapped and tied to the network token.
If you wish to get the raw PAN, consider the ShieldConex Tokenization & Network Tokens approach.
To ensure maximum security, each request for credentials associated with the same network token returns a unique cryptogram for each CIT.
Cryptogram Usage | CITs and MITs
Getting a cryptogram is required for a CIT transaction where the rest of the
networkTokenobject fields are typically stored for subsequent MITs. However, in this case being a large ISV, you could be subject to increased PCI DSS scope requirements.Also, see Data Efficiency for the minimal set of object fields needed for transaction processing.
OverviewCustomer initiated transactions (CIT), as the name suggests, are initiated by the customer (enhancing authorization and authentication), usually as CNP transactions. Examples include online purchases, in-store purchases and mobile payments.
Merchant initiated transactions (MIT) play a crucial role in situations where the merchant needs to charge the customer on a regular basis or perform transactions without requiring repeated customer interactions. These transactions reduce friction for customers by eliminating the need for repeated manual entries.
MITs are processed based on a prior agreement with the customer.
Request
GET /api/network-token-bundle/{networkTokenBundleId}/payment-credentials
{
"headers": {
"Authorization": "Basic {Base64_Encoded_API_KEY}",
"Content-Type": "application/json",
"scx-client-reference": "cl000744"
}
}
Response
{
"messageId": "1202506261455281262126996",
"networkTokenBundleId": "7030070000047325639",
"networkToken": {
"networkTokenId": "364C5478E9336F06E063AF598E0A96FB",
"networkTokenState": "ACTIVE",
"tokenizedNumber": "4895370019675690",
"expirationMonth": "12",
"expirationYear": "2026",
"type": "visa",
"cryptogram": "AwAAAAACgYVzzhAF9eD8grEAAAA=",
"eci": "07",
"requestorId": "40000000082",
"card": {
"suffix": "5639",
"expirationMonth": "12",
"expirationYear": "2026"
}
},
"card": {
"number": "462294XXXXXX5639"
},
"issuer": {
"paymentAccountReference": "V0010013025078536357001803531"
}
}
ECI: Electronic Commerce Indicator
The ECI value indicates the level of security used in an electronic commerce transaction. It helps the card issuer determine whether the transaction was authenticated and the associated (low or high) risk level. This value is typically represented by a 2-digit numeric code.
For Visa ECI values, check out 5.1 Electronic Commerce Indicator (ECI).
For Mastercard ECI values, see E-Commerce Commerce Indicator.
Delete a Network Token Bundle
Some of the reasons to delete a network token can include:
- Customer Request for Data Deletion (PCI DSS Compliance)
- Managing Payment Method Updates
- Deactivating Fraudulent or Compromised Payment Tokens
- End of Business Relationship or Account Termination
- Clearing Inactive or Expired Tokens for System Optimization
- Revoking Access After Payment Gateway Changes
DELETE /api/network-token-bundle/{networkTokenBundleId}
{
"headers": {
"Authorization": "Basic {Base64_Encoded_API_KEY}",
"Content-Type": "application/json",
"scx-client-reference": "cl000744"
}
}
The request returns 200 on success.
Data Efficiency
Processing MITs requires the merchant to store the encrypted data in their databases for recurring payments or similar.
It is essential to focus on how efficiently the merchant is managing and processing their data both from the storage and performance side of things as well as reducing the network bandwidth.
For this reason, we strongly recommend using the following minimal set of response fields for transaction processing with network tokens.
Customer Initiated Transactions (CIT)
| Field | Description |
|---|---|
$.networkToken.tokenizedNumber | Tokenized Card Number. This is never the raw PAN. It is encrypted and mapped internally by the Network Token Service to the real card. |
$.networkToken.expirationMonth | Token Expiry Month |
$.networkToken.expirationYear | Token Expiry Year |
$.networkToken.eci | This may be optional but best practice. It could depend on processor. Typically, the merchant is burning money by not including it. Also, check out the note on ECI: Electronic Commerce Indicator above for its usage. |
$.networkToken.cryptogram | See Get Payment Credentials. |
$.networkToken.requestorId | A unique identifier for your business when you request network tokens from Visa and Mastercard. |
Merchant Initiated Transactions (MIT)
| Field | Description |
|---|---|
$.networkToken.tokenizedNumber | Tokenized Card Number. This is never the raw PAN. It is encrypted and mapped internally by the Network Token Service to the real card. |
$.networkToken.expirationMonth | Token Expiry Month |
$.networkToken.expirationYear | Token Expiry Year |
$.networkToken.eci | This may be optional but best practice. It could depend on processor. Typically, the merchant is burning money by not including it. Also, check out the note on ECI: Electronic Commerce Indicator above for its usage. |
$.networkToken.requestorId | A unique identifier for your business when you request network tokens from Visa and Mastercard. |
Compatibility: networkTokenBundleId vs networkTokenId
It is important to outline that networkTokenBundleId is used in the context of ShieldConex API while networkTokenId is primarily used for compatibility purposes in cases where the merchant transfers to another network token provider. Most importantly, Bluefin ShieldConex is not forcing the merchant to strictly use a specific network token provider.
Difference between networkTokenBundleState and networkTokenState
networkTokenBundleState and networkTokenStateGiven that there can be other types of tokens, we have added networkTokenBundleState for the portability of ShieldConex API. If you are working with network tokens, the networkTokenState matches the networkTokenBundleState.
Token Expiry vs Card Expiry
From the responses above, it is crucial to understand the difference between $.networkToken.expirationMonth and $.networkToken.card.expirationMonth.
As the JSON path indicates, the expirations tied to the $.networkToken (representing the life-span of the network token) are used for transaction processing with network tokens whereas the expiry data of $.networkToken.card is particular to the card itself. Therefore, these two are unrelated.
This distinction is critical since network tokens do not expire based on the card expiry if the cardholder changes the card information. For more detail, see ShieldConex® Network Tokens | Overview.
Certification vs Production Responses
The response structures and JSON schema are identical for both certification and production environments of ShieldConex API except that the $.networkToken.tokenizedNumber response field of Get Payment Credentials endpoint is masked in certification. For example, 489537XXXXXX5690.
ShieldConex Tokenization & Network Tokens API
When a merchant is considering a future switch to a different payment processor, ShieldConex provides flexibility. In such cases, the preferred option is to return both the ShieldConex tokens and the associated network token. As a double-edged sword, this ensures that tokenized data remains usable across processors. ShieldConex tokens play a key role in enabling this portability.
For more information, also see ShieldConex | Tokenization Explained and ShieldConex® Orchestration.
Did you know?
To date, network tokens are used in roughly 30% of Visa and Mastercard transactions.
In combination with Network Tokens, ShieldConex utilizes its tokenization solution so that the customer has the flexibility to switch to a different payment processor, thus delivering processor independence.
If a network token times out or fails, the Tokenization API returns ShieldConex tokens, resulting in a non-network token transaction. ShieldConex tokens are, either way, included once a network token is successfully returned.
Tokenization
With a template field (be it Card Information or Custom Field) as FPT(Format Preserving Tokenization) + Network Tokens, the following request returns both ShieldConex tokens and Network Tokens in response by Creating a Network Token.
Request
POST /api/tokenization/tokenize
Omit Flag
The tokenization API endpoint can also take the
omitflag in the query parameters. For example,POST
https://secure{-*}.shieldconex.com/api/tokenization/tokenize?omit=1The omit flag used in the tokenization API has had 2 options in the past - when set to
0, the tokens are returned in the response to the request, and when set to1, the tokens would be cached by Bluefin to be retrieved asynchronously. The default value is0orfalse. We have added an additional option to set this value to2, which will result in the tokens being returned in the response and cached by Bluefin for up to 1 hour.
{
"reference":"myref",
"templateRef":"128ac7acefdd0825a21c126ee1fe6c09",
"values":[
{"name":"card_number","value":"4622943123155639"},
{"name":"card_exp","value":"122026"},
{"name":"card_cvv","value":"1234"}
]
}
Note
If Creating a Network Token fails, the ShieldConex tokens are included regardless where the
networkTokenBundleis dropped.
Response
ShieldConex Iframe
This endpoint is also used as part of the ShieldConex Iframe and it returns the same data below, making it flexible across all interfaces.
For more, see iFrame SDK & Tokenization and Iframe-based secure tokenization and detokenization processing.
As mentioned above, the response is the combination of the ShieldConex tokens and Creating a Network Token response.
{
"messageId": "1202506261456311242669602",
"reference": "myref",
"bfid": "djI6MT...",
"values": [
{
"name": "card_number",
"value": "9246266530387677"
},
{
"name": "card_exp",
"value": "648413"
},
{
"name": "card_cvv",
"value": "126"
}
],
"networkTokenBundle": {
"networkTokenBundleId": "7030070000047325639",
"networkTokenBundleState": "ACTIVE",
"networkToken": {
"networkTokenState": "ACTIVE",
"tokenizedNumber": "489537XXXXXX5690",
"expirationMonth": "12",
"expirationYear": "2026",
"type": "visa",
"card": {
"suffix": "5639",
"expirationMonth": "12",
"expirationYear": "2026"
}
},
"issuer": {
"paymentAccountReference": "V0010013025078536357001803531"
},
"metadata": {
"creator": "testbluefin_sandbox001"
}
}
}
Without detokenizing ShieldConex tokens, the networkTokenBundleId can be used separately to get the payment credentials for the merchant to process a payment on behalf of the customer.
For example,
Request
scx-client-referenceThis header is required and is the Client ID tied to the Partner used for API Authentication.
GET /api/network-token-bundle/7030070000047325639/payment-credentials
{
"headers": {
"Authorization": "Basic {Base64_Encoded_API_KEY}",
"Content-Type": "application/json",
"scx-client-reference": "cl000744"
}
}
Response
{
"messageId": "1202506261457491241462510",
"networkTokenBundleId": "7030070000047325639",
"networkToken": {
"networkTokenId": "364C5478E9336F06E063AF598E0A96FB",
"networkTokenState": "ACTIVE",
"tokenizedNumber": "4895370019675690",
"expirationMonth": "12",
"expirationYear": "2026",
"type": "visa",
"cryptogram": "AwAAAAACix/WzREF9eD8grEAAAA=",
"eci": "07",
"requestorId": "40000000082",
"card": {
"suffix": "5639",
"expirationMonth": "12",
"expirationYear": "2026"
}
},
"card": {
"number": "462294XXXXXX5639"
},
"issuer": {
"paymentAccountReference": "V0010013025078536357001803531"
}
}
Detokenization
ShieldConex® Orchestration
Detokenization call with the sensitive card holder data is a use case with ShieldConex® Orchestration where the detokenized values are forwarded to the payment processor if the network tokens are not created and provisioned successfully, payment credentials are not received, or similar.
For more information, refer to ShieldConex® Orchestration.
Non-Sensitive data & Payment CredentialsAnother use case is when the merchant wants to get other raw non-sensitive data with the token payment credentials if they are offering a subscription service keeping other data encrypted in their database or similar.
{ "reference": "myref", "bfid": "djI6MT...", "values": [ { "name": "card_holder_name", "value": "2342342311111" }, { "name": "card_holder_last_name", "value": "342341234324" } ], "networkTokenBundle": { "networkTokenBundleId": "7030070000047325639" } }
The detokenize API call returns both the detokenized values and the network token payment credentials.
Request
POST /api/tokenization/detokenize
{
"reference": "myref",
"bfid": "djI6MT...",
"values": [
{
"name": "card_number",
"value": "9246266530387677"
},
{
"name": "card_exp",
"value": "648413"
},
{
"name": "card_cvv",
"value": "126"
}
],
"networkTokenBundle": {
"networkTokenBundleId": "7030070000047325639"
}
}
Response
{
"messageId": "1202506261458201241558872",
"reference": "myref",
"values": [
{
"name": "card_number",
"value": "4622943123155639"
},
{
"name": "card_exp",
"value": "122026"
},
{
"name": "card_cvv",
"value": "242"
}
],
"networkTokenBundle": {
"networkTokenBundleId": "7030070000047325639",
"networkToken": {
"networkTokenId": "364C5478E9336F06E063AF598E0A96FB",
"networkTokenState": "ACTIVE",
"tokenizedNumber": "4895370019675690",
"expirationMonth": "12",
"expirationYear": "2026",
"type": "visa",
"cryptogram": "AwAAAAACn+kQVOQF9eD8grEAAAA=",
"eci": "07",
"requestorId": "40000000082",
"card": {
"suffix": "5639",
"expirationMonth": "12",
"expirationYear": "2026"
}
},
"card": {
"number": "462294XXXXXX5639"
},
"issuer": {
"paymentAccountReference": "V0010013025078536357001803531"
}
}
}
Updated 5 months ago
